PCC TF-1/BPPC
HIMSS and RSNA
Integrating the Healthcare Enterprise
IHE Patient Care Coordination
Technical Framework
Basic Patient Privacy Consents
Revision 2.0
2006-2007
Draft
Volume 1
HIMSS and RSNA
Integrating the Healthcare Enterprise
IHE Patient Care Coordination
Technical Framework
Volume I
Revision 3.0
2008-2009
Public Comment
- (PCC TF-1/Preface)Preface to Volume I of the PCC Technical Framework
- (PCC TF-1/Introduction)Introduction to the PCC Technical Framework
- (PCC TF-1/About)About the Patient Care Coordination Integration Profiles
- (PCC TF-1/Dependencies)Dependencies of the PCC Integration Profiles
- (PCC TF-1/Overview)PCC Integration Profiles Overview
- (PCC TF-1/History)History of Annual Changes
- (PCC TF-1/Product Implementations)Product Implementations
BPPC Integration Profile
The document sharing infrastructure provided by XD* allow for the publication and use of clinical documents associated with a patient. The XDS/XDR system requires that the Affinity Domain create and agree to a single policy (See IHE-ITI Vol 1:Appendix L). The Affinity Domain Policy is enforced in a distributed way through the inherent access controls of the systems involved in the Affinity Domain. This profile will use terms consistent with ISO 22600 - Privilege Management and Access Control (PMAC), but is not restricted to systems that implement PMAC. The systems involved in XDS are expected to support sufficient Access Controls to carry out the Policy of the Affinity Domain.
Today this single Affinity Domain Policy restriction means that much of the useful data is not entered into the XDS, or that the access to this data is too liberally allowed. This profile allows for the Affinity domain to have a small number of privacy consents. This allows for more flexibility to support some patient concerns, while providing an important and useful dataset to the healthcare provider.
Healthcare providers utilize many different sets of data to carry out treatment, billing, and normal operations. This information may include patient demographics, contacts, insurance information, dietary requirements, general clinical information and sensitive clinical information. This information may be published to XDS as independent documents under different privacy consent policies.
Healthcare providers in different functional roles will have different needs to access these documents. For example, administrators may need to be able to access the patient demographics, billing and contact documents. Dietary staff will need access to the dietary documents but would not need access to insurance documents. General care providers will want access to most clinical documents, and direct care providers should have access to all clinical documents.
This profile provides a mechanism by which an affinity domain can create a basic vocabulary of codes that identify affinity domain privacy consent policies with respect to information sharing. Each privacy consent policy should identify in legal text what are the acceptable re-disclosure uses, which functional roles may access a document and under which conditions. Each privacy consent will be assigned a unique XDS Affinity Domain wide OID by the administration of the XDS Affinity Domain with care to respect any inheritance of previous privacy consent policies. Future profiles may include structured and coded language that can be used to support dynamic understanding of the patient's directives (see HL7 and OASIS).
Basic Patient Privacy Consent Use-Cases
This section gives examples of some possible patient privacy consent policies and how the systems publishing documents and using documents might act. This is an informative section and should not be interpreted as the only way to implement the BPPC profile.
Wet Signature
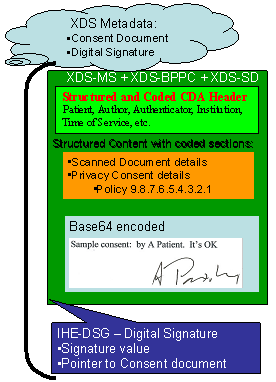
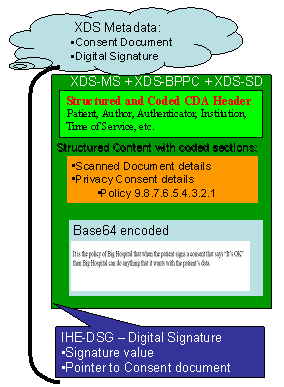
Big Hospital has not yet fully digitized their patient consents process. They have a paper document that describes their Privacy Consent Policy. In our example this Privacy Consent Policy will be referenced as policy 9.8.7.6.5.4.3.2.1. Our example is ridiculous, but points out that the content of the policy is legal text, and that we provide no structured or coded way to interpret. This policy looks like:
| It is the policy of Big Hospital that when a patient signs a consent that says "It's OK" then big hospital can do anything it wants with the patient's data. |
Big Hospital has the patient acknowledge this consent through ink on paper. This act produces the Patient Privacy Consent, For Example:
| Sample Consent: by A. Patient. It's OK |
This acknowledgement is captured according to the XDS-SD profile, with the additional parameters specified in the BPPC profile also applied to the CDA wrapper. This is registered with the XDS as proof that the patient has consented to policy 9.8.7.6.5.4.3.2.1. This acknowledgement will have its own OID as any document registered in XDS will have, but this instance OID is not further used.
This example is available on the IHE wiki for educational purposes.
If the hospital wants to further provide authenticity protections they may apply a DSG digital signature to the whole package with the appropriate purpose and signed by an appropriate signing system/person.
The following shows this graphically:
Implied Consent vs Explicit Consent
This profile supports both Implied Consent as well as Explicit Consent environments. In order to provide a profile with global appeal we have supported both environments. In an implied consent environment a Document Consumer will not find an instance of a Patient Privacy Consent document in the XDS, as capturing the act of consenting would not be required. This may be true in an Explicit Consent environment as well in cases where getting the explicit consent is delayed due to medical reasons (e.g. emergency).
In an implied Consent environment, the clinical documents submitted to the XDS would need to be marked with the general use consent, where other documents may have additional explicit consents.
Electronic Patient Consent
In this use case we move forward to a XDS Affinity Domain where the patient has a unique Public Certificate. This use case has the patient digitally signing the consent. In this case we don't capture a wet signature. For this example we include the PDF of the consent text, and this is what the patient signs. The patient's digital signature is captured using the IHE Digital Signature (DSG) profile, as shown below:
Administrative Use
Healthcare providers utilize many different sets of data to carry out the treatment, billing, and normal operations. When a patient presents, often the patient must fill out volumes of information used for patient demographics, contacts, and insurance.
For this example we might illustrate a registration system that captures a scanned image of the patient's insurance card. This scanned image can be submitted to the XDS using the confidentiality code indicating that it is available for administrative uses. This registration system could additionally capture the typical demographics and such in a form of coded clinical document that is also published as available for administrative use. Both of these documents don't have clinical information and thus wouldn't need to be restricted to direct care providers.
Now that we have shown how this information can be captured. We can see cases where the patient presents at a different clinic in the same XDS Affinity Domain. The administrative staff can now query the XDS and simply confirm that the information is the same.
Clinical Support Staff Use
The patient when staying for a few days might have special dietary needs based on their conditions. These dietary needs could be documented in the XDS and marked as for clinical support staff. This document could be accessed by the dietitian when preparing the meals.
Mixed Patient Privacy Consents
As can be seen by the use-cases shown already over time an XDS Affinity Domain may have a mixture of implied consent, wet signature consents and patient digital signature consents. The XDS Affinity Domain will also have multiple generations of patient consents.
Policies in an environment with comprehensive access controls
An Affinity Domain may have jurisdictional or organizational policies that require support for more complex patient privacy consent policies. These privacy policies may require that a patient explicitly consent to disclosure of protected or sensitive health information to specific entities. The BPPC profile provides a starting point for implementing these types of privacy consent policies, but does not explicitly specify how additional information needed to enforce the policy would be conveyed.
For example, in a jurisdiction that requires explicit patient consent to disclose psychotherapy notes:
- The Affinity Domain would define sufficiently explicit functional roles as well as contextual and user specific role information to support these policies in the consent provided.
- The Affinity Domain would include a sensitivity marker for psychotherapy notes and may only permit access by the functional role
- "named entity", where the named entity identifier must match the identifier of the named entity in the patient's associated consent document associated with the patient's health document;
- an "unnamed entity" based on a time limited and non-transferrable "shared secret key" supplied to the entity by the patient and authenticated by some algorithm the informaiton in the patient's associated consent document; or
- an emergency provider who submits a "break the glass key" administered by the Affinity Domain that has an appropriate audit trail with documentation of the provider's reason and context for use per Affinity Domain policy.
The psychotherapy notes would then be submitted to the XDS using the confidentiality code indicating that it is available only to these entities.
In addition to document type level sensitivity markers, e.g., psychotherapy notes, an Affinity Domain might also support sensitivity markers for types of health information that might be included in documents of many types. There may be sensitivity markers for any document that includes diagnosis, procedure, medication, location, or provider information which the patient believes may indicate that the patient has genetic, substance use, HIV-AIDs, mental health or other conditions, which the patient wishes to mask. Another use for sensitivity markers is for victims of abuse who wish to mask all records containing their demographic information.
Privacy Access Policies (Informative)
One possible implementation may have a collection of policies and sensitivity markers form an access control matrix. A simple access control matrix is shown in Table 5.2 1.
| Sensitivity Functional Role |
Billing Information | Administrative Information | Dietary Restrictions | General Clinical Information | Sensitive Clinical Information | Research Information | Mediated by Direct Care Provider |
| Administrative Staff | X | X | |||||
| Dietary Staff | X | X | |||||
| General Care Provider | X | X | X | ||||
| Direct Care Provider | X | X | X | X | X | ||
| Emergency Care Provider | X | X | X | X | X | ||
| Researcher | X | ||||||
| Patient or Legal Representative | X | X | X | X | X |
The matrix can be sliced vertically. By slicing the matrix vertically (by sensitivity marker), a single patient consent policy (aka. sensitivity marker) vocabulary can be established. This vocabulary must then be configured in the XDS Affinity Domain.
Using the example above, the privacy consent policies would be.
| Privacy Consent Policy | Description |
| Billing Information | May be accessed by administrative staff and the patient or their legal representative. |
| Administrative Information | May be accessed by administrative or dietary staff or general, direct or emergency care providers, the patient or their legal representative. |
| Dietary Restrictions | May be accessed by dietary staff, general, direct or emergency care providers, the patient or their legal representative. |
| General Clinical Information | May be accessed by general, direct or emergency care providers, the patient or their legal representative. |
| Sensitive Information | May be accessed by direct or emergency care providers, the patient or their legal representative. |
| Research Information | May be accessed by researchers. |
| Mediated by Direct Care Provider | May be accessed by direct or emergency care providers. |
The access control matrix can also be sliced horizontally by functional role. This requires that a separate vocabulary for document Privacy Consent Policy be configured in the XDS Affinity Domain.
| Privacy Consent Policy | Description |
| Administrative Staff | May access documents that describe their sensitivity with the Billing Information or Administrative Information code. |
| Dietary Staff | May access documents that describe their sensitivity with the Administrative Information or Dietary Restrictions codes. |
| General care providers | May access documents that describe their sensitivity with the Administrative Information, Dietary Restrictions or General Clinical Information codes. |
| Direct care providers | May access documents that describe their sensitivity with the Administrative Information, Dietary Restrictions, General Clinical Information, or Sensitive Clinical Information codes. |
| Emergency care providers | May access documents that describe their sensitivity with the Administrative Information, Dietary Restrictions, General Clinical Information, or Sensitive Clinical Information codes. |
| Researchers | May access documents that describe their sensitivity with the Research Information code. |
| Patient (or legal representative) | May access documents that describe their sensitivity with the Administrative Information, Dietary Restrictions, General Clinical Information, or Sensitive Clinical Information codes. |
Other divisions of the access control matrix are possible, so long as a Privacy Consent Policy covers each cell granting access in the matrix.
References
The following list of references is provided as good references to understand the terms and concepts presented here. These references are not required by this profile.
- ISO/TS 21298 "Health informatics – Functional and structural roles".
- ISO/TS 22600 "Health Informatics – Privilege Management and Access Controls".
- CEN prEN 13606-4 "Health informatics — Electronic health record communication — Part 4: Security requirements and distribution rules"
Creating Privacy Consent Policies
A Privacy Consent Policy shall identify who has access to information, and what information is governed by the policy (e.g., under what conditions will a document be marked as containing that type of information). The XDS Affinity Domain shall publish privacy Consent Policies. The mechanism for publishing these policies is not described by this profile. The Privacy Consent Policies written by the XDS Affinity Domain must be able to be implemented by the technologies in all of the systems that have access to the XDS Affinity Domain. This means that the Privacy Consent Policies must be created with great care to ensure they are enforceable.
The implementation of Privacy Consent Polices under this profile makes it strongly advisable that policies describe under what situations a functional role shall have access to information, and do not include situations in which a functional role is not granted access. Take care when writing access control policies. The two policy statement examples below illustrate the problem.
- A Researcher may >>only<< access documents that describe their sensitivity with the Clinical Trial 1 code.
- A Researcher may >>only<< access documents that describe their sensitivity with the Research Project 1 code.
The first policy grants access to a researcher to one class of documents (those marked with the Clinical Trial 1 code), and due to the word "only", effectively revokes access to all other documents. The second policy does the same thing (for Research Project 1), and revokes access to all other documents. These two policies cannot be applied at the same time, as they are incompatible with each other. The solution is to strike the word >>only<< and thus the two Privacy Consent Policies are able to be aggregated.
An XDS Affinity Domain may have legacy documents that were published prior to all systems supporting the BPPC Profile, and thus will have confidentiality codes not defined under the BPPC Profile (e.g. For example, "N" from 2.16.840.1.113883.5.25). The XDS Affinity Domains will need to provide Privacy Consent Policies for granting access to documents that use these non-BPPC confidentiality code values.
Affinity domains should also determine their strategy for addressing the changing of Privacy Consent Policies and the policy vocabularies.
Finally, Privacy Consent Policies used within an XDS Affinity Domain will very likely be different than those used with the XDM or XDR Profiles. The patient may provide a consent given to share information on media to the provider creating the media for specific use, rather than for more general sharing within an XDS Affinity Domain. When transferring information that originated in an XDS Affinity Domain to media (XDM), the Privacy Consent Policies found in the XDS Affinity Domain might be changed during the publication process. There are also differences in the sensitivity that should be considered for consents shared on media or transmitted through XDR and those shared in an XDS affinity domain. See the section Security Considerations later in this volume for more details.
Implementation of Access Control
Consumers of documents that implement this profile are required to enforce access control based on the policies described by the Affinity Domain. This is because the consumers of the documents are best aware of the functional role, how the data will be used, the relationship between provider and patient, the urgency of access, etc. The mechanism by which consumers associate individual users with functional roles is not within the scope of this profile. However it does allow for mechanisms to be used that take into account the structural role of the user, their association with the patient, the functional role that they are assigned with the session in which they are accessing data, and the declared sensitivity of the data being protected.
Actors/Transaction
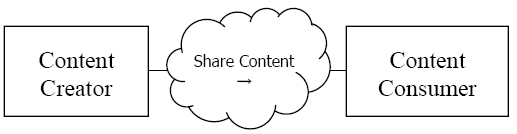
There are two actors in the BPPC profile, the Content Creator and the Content Consumer. Content is created by a Content Creator and is to be consumed by a Content Consumer. The sharing or transmission of content from one actor to the other is addressed by the appropriate use of IHE profiles described below, and is out of scope of this profile. A Document Source or a Portable Media Creator may embody the Content Creator Actor. A Document Consumer, a Document Recipient or a Portable Media Importer may embody the Content Consumer Actor. The sharing or transmission of content or updates from one actor to the other is addressed by the use of appropriate IHE profiles described in the section on Content Bindings with XDS, XDM and XDR.
Options
| Actor | Option |
|---|---|
| Content Consumer | View Option (1) |
| Document Import Option (1) | |
| Section Import Option (1) | |
| Discrete Data Import Option (1) | |
| Content Creator | Referral Option (1) |
| Discharge Summary Option (1) |
Content Consumer Options
View Option
This option defines the processing requirements placed on Content Consumers for providing access, rendering and management of the medical document. See the View Option in PCC TF-2 for more details on this option.
A Content Creator Actor should provide access to a style sheet that ensures consistent rendering of the medical document content as was displayed by the Content Consumer Actor.
The Content Consumer Actor shall be able to present a view of the document using this style sheet if present.
Document Import Option
This option defines the processing requirements placed on Content Consumers for providing access, and importing the entire medical document and managing it as part of the patient record. See the Document Import Option in PCC TF-2 for more details on this option.
Section Import Option
This option defines the processing requirements placed on Content Consumers for providing access to, and importing the selected section of the medical document and managing them as part of the patient record. See the Section Import Option in PCC TF-2 for more details on this option.
Discrete Data Import Option
This option defines the processing requirements placed on Content Consumers for providing access, and importing discrete data from selected sections of the medical document and managing them as part of the patient record. See the Discrete Data Import Option in PCC TF-2 for more details on this option.
Cross Enterprise Document Sharing, Media Interchange and Reliable Messaging
Actors from the ITI XDS, XDM and XDR profiles embody the Content Creator and Content Consumer sharing function of this profile. A Content Creator or Content Consumer may be grouped with appropriate actors from the XDS, XDM or XDR profiles to exchange the content described therein. The metadata sent in the document sharing or interchange messages has specific relationships or dependencies (which we call bindings) to the content of the clinical document described in the content profile.
The Patient Care Coordination Technical Framework defines the bindings to use when grouping the Content Creator of this Profile with actors from the IHE ITI XDS, XDM or XDR Integration Profiles.
| Content | Binding | Actor | Optionality |
| Consent to Share Inforamation | Consent Binding to XD* | Content Creator | R |
| Content Consumer | R | ||
| Medical Documents | Medical Document Binding to XD* | Content Creator | R |
| Content Consumer | R |
Consent Content Module
A consent document is a kind of medical document, and shall conform to the requirements of the Consent content module specified in this profile. The content of a consent document shall include the effective time of the consent and coded vocabulary identifying the policies consented to (OID). The content of the consent document may include a text description of what the patient has consented to, and either a facsimile of a wet signature, or a digital signature by the patient (or legal representative). The consent if signed shall use the IHE ITI DSG profile.
BPPC Process Flow
The BPPC profile uses the normal process flow of the XD* profiles, depending upon which bindings have been declared.
- Administrative tasks prior to BPPC use
- The Affinity Domain will write and agree to the Affinity Domain Policy (lots of lawyers involved).
- The Affinity Domain Policy will include a small set of Privacy Consent Policies (more lawyers). These are text documents very similar to the privacy consent documents used today.
- Each Privacy Consent Policy will be given an XDS Affinity Domain unique identifier (OID)
- The Affinity Domain Policy and all of the Privacy Consent Policies will be published in a way consistent with the Affinity Domain's Policy. It is expected that this will be sufficiently public to support local regulation.
- Patient consents to a policy
- The Patient will be presented with the Affinity Domain – Patient Privacy Consent Policies.
- The Patient will agree to one or more of the Privacy Consent Policies. In most regions the patient must be fully informed and acknowledge the privacy consent. In some regions there is implied consent, and thus there is no need to capture a patient's consent.
- A system that captures patient privacy consents will capture this act in a BPPC Patient Privacy Consent Document.
- XDS Metadata
- authorPerson is the patient or legal guardian that is agreeing to the consent.
- classCode indicates this is a consent document
- confidentialityCode may indicate other consent OIDS that control this consent document
- eventCodeList indicates the Privacy Consent Policy identifier (OID)
- legalAuthenticator would be the digital signer if used, or the identity of the Affinity Domain representative that is confirming that the patient is agreeing.
- serviceStartTime and serviceStopTime indicate when this consent is effective.
- Patient Privacy Consent Document
- template ID = "1.3.6.1.4.1.19376.1.5.3.1.1.7 "
- The patient or legal guardian that is agreeing to the consent is identified as the author of the consent document.
- Any witness to this consent may be captured (i.e. participant typeCode='WIT')
- authorization indicates that this is a consent act
- Effective time is set
- When the privacy consent is first effective. This effective date may be retroactive based on the XDS Affinity Domain Policy.
- If necessary, when the privacy consent is expected to elapse
- If wet signature is used, the XDS-SD profile will be used to scan the paper and encode it into the consent document
- the XDS-SD CDA attributes are combined with the BPPC CDA attributes.
- If digital signature is used the DSG profile will be used to sign the consent document. This is an additional document that is published. This may be published in the same submission set, or may come after based on workflow.
- XDS Metadata
- System checking on a patient's consent status
- When a system/individual wants to know if a specific patient has consented it can do a query for consent documents on that patient.
- Note if the local regulations allow, some XDS Affinity Domains may not publish the consent documents, so systems should be able to handle these configurations.
- Note if the local regulations allow, some patients may have documents shared before informed consent can be captured.
- Clinical documents are published into XDS Affinity Domain
- When clinical documents are published into XDS an assessment must be done to determine which of the XDS Affinity Domain – Privacy Consent Policies would allow the documents to be published.
- In some XDS Affinity domains this may require that the system check that a patient has indeed consented to the specific policy (see 3)
- This is likely based on human configuration of the document source system.
- The XDS Metadata – confidentialityCode - will include the OIDS of the appropriate (determined by the XDS Affinity Domain Policy) Privacy Consent Policy identifier (OID)
- The XDS Registry will validate that the confidentialityCode is one approved for use within the XDS Affinity Domain.
- When clinical documents are published into XDS an assessment must be done to determine which of the XDS Affinity Domain – Privacy Consent Policies would allow the documents to be published.
- Clinical documents are used from the XDS Affinity Domain
- When a system queries the XDS Affinity Domain it should utilize the confidentialityCode in the queries to restrict the documents returned to those that the system can utilize
- For Example: If the system is a research application, then it should set the confidentialityCode in the query to the list of XDS Affinity Domain Policy identifiers (OIDs) that would allow for the documents to be used for the research.
- Even if the confidentialityCode is not specified, the system implementing the Document Consumer actor is still bound to enforce the XDS Affinity Domain Policies.
- The consumer system will enforce access controls based the returned metadata-confidentialityCode, system type, user, context, and any number of other factors that the system is capable of enforcing.
- When a system queries the XDS Affinity Domain it should utilize the confidentialityCode in the queries to restrict the documents returned to those that the system can utilize
Grouping with Other Profile Actors
The capturing of the patient consenting could be futher covered by use of the IHE Digital Signature content profile (DSG). Systems should be prepared to see DSG related content associated with the Patient Privacy Consent document.
Security Considerations
Consents stored in an XDS affinity domain are also governed by privacy policies. The content of a Privacy Consent may itself contain sensitive information. For example, a terminally ill patient may decide that his prognosis should not be shared with his family members, but that other information may be. Sharing the Privacy Consent Act with family members would potentially inform them of a negative prognosis.
However, Privacy Consent Acts stored in the clear on media (XDM), or otherwise transmitted through XDR should not contain sensitive information. The rationale is that the receiver of the information must be able to read the consent that was used to share this information in order to understand how they must treat the information with respect to their own Privacy Consent Policies.
Implementation of Privacy Consent Policies within a healthcare environment has different considerations and risks than implementing similar access control policies within other non-treatment environments. This is for the simple reason that failing to provide access to critical healthcare information has the risk of causing serious injury or death to a patient. This risk must be balanced against the risk of prosecution or lawsuit due to accidental or malicious disclosure of private information. The XDS Affinity Domain should take care in writing their Privacy Consent Policies to avoid this.
One mitigation strategy often adopted in healthcare provides Accountability through Audit Controls. That is to say that healthcare providers are trusted not to abuse their access to private information, but that this is followed up by a policy of monitoring healthcare provider accesses to private information to ensure that abuse does not occur. This strategy reduces the risk of serious death or injury due to lack of access to critical healthcare information, at the increased risk of disclosure of private information. This is why the ITI Technical Committee created the Audit Trail and Node Authentication (ATNA) Integration profile, and furthermore, why that profile is a requirement of XDS and related profiles.
Another risk that must be resolved by an affinity domain is how to address the issues of sharing truly sensitive information in a registry (e.g., for VIP patients, or sensitive data). One strategy that might be recommended is that truly sensitive data not be shared within the XDS Affinity Domain, directed communications using XDR or XDM may be more appropriate.
Appendix A - Actor Descriptions
Actors are information systems or components of information systems that produce, manage, or act on information associated with operational activities in the enterprise.
- Content Creator
- The Content Creator Actor is responsible for the creation of content and transmission to a Content Consumer.
- Content Consumer
- A Content Consumer Actor is responsible for viewing, import, or other processing of content created by a Content Creator Actor.
- Clinical Data Consumer
- A clinical data consumer makes use of clinical patient data.
- Clinical Data Source
- A Clinical Data Sources maintains patient information about vital signs, problem and allergies, results from diagnostic tests (e.g., Lab, Imaging, or other test results), medications, immunizations or historical or planned visits and procedures.
Appendix B - Transaction Descriptions
Transactions are interactions between actors that transfer the required information through standards-based messages. The PCC Technical Framework does not define any specific transactions, as these are assumed to be carried out through the use of transactions defined in other IHE Profiles.
- Query Existing Data
- Request information about recent patient information, used to obtain vital signs measurements, problems and allergies, diagnostic results, medications, immunizations, or procedures or visits relevant for a patient. The query may request information about some or all of the above topics, or may request information on a specific topic, or one entered for a specific encounter or date range.
Appendix C - How to Prepare an IHE Integration Statement
IHE Integration Statements are documents prepared and published by vendors to describe the conformance of their products with the IHE Technical Framework. They identify the specific IHE capabilities a given product supports in terms of IHE actors and integration profiles described in the technical frameworks of each domain.
Users familiar with these concepts can use Integration Statements to determine what level of integration a vendor asserts a product supports with complementary systems and what clinical and operational benefits such integration might provide. Integration Statements are intended to be used in conjunction with statements of conformance to specific standards (e.g., HL7, IETF, DICOM, W3C, etc.).
IHE provides a process for vendors to test their implementations of IHE actors and integration profiles. The IHE testing process, culminating in a multi-party interactive testing event called the Connectathon, provides vendors with valuable feedback and provides a baseline indication of the conformance of their implementations. The process is not intended to independently evaluate, or ensure, product compliance. In publishing the results of the Connectathon and facilitating access to vendors' IHE Integration Statements, IHE and its sponsoring organizations are in no way attesting to the accuracy or validity of any vendor's IHE Integration Statements or any other claims by vendors regarding their products.
IMPORTANT -- PLEASE NOTE: Vendors have sole responsibility for the accuracy and validity of their IHE Integration Statements. Vendors' Integration Statements are made available through IHE simply for consideration by parties seeking information about the integration capabilities of particular products. IHE and its sponsoring organizations have not evaluated or approved any IHE Integration Statement or any related product, and IHE and its sponsoring organizations shall have no liability or responsibility to any party for any claims or damages, whether direct, indirect, incidental or consequential, including but not limited to business interruption and loss of revenue, arising from any use of, or reliance upon, any IHE Integration Statement.
Structure and Content of an IHE Integration Statement
An IHE Integration Statement for a product shall include:
- The Vendor Name
- The Product Name (as used in the commercial context) to which the IHE Integration Statement applies.
- The Product Version to which the IHE Integration Statement applies.
- A publication date and optionally a revision designation for the IHE Integration Statement.
- The following statement: "This product implements all transactions required in the IHE Technical Framework to support the IHE Integration Profiles, Actors and Options listed below:"
- A list of IHE Integration Profiles supported by the product and, for each Integration Profile, a list of IHE Actors supported. For each integration profile/actor combination, one or more of the options defined in the IHE Technical Framework may also be stated. Profiles, Actors and Options shall use the names defined by the IHE Technical Framework Volume I. (Note: The vendor may also elect to indicate the version number of the Technical Framework referenced for each Integration Profile.)
Note that implementation of the integration profile implies implementation of all required transactions for an actor as well as selected options.
The statement shall also include references and/or internet links to the following information:
- Specific internet address (or universal resource locator [URL]) where the vendor's Integration Statements are posted
- URL where the vendor's standards conformance statements (e.g., HL7, DICOM, etc.) relevant to the IHE transactions implemented by the product are posted.
- URL of the IHE Initiative's web page for general IHE information www.himss.org/ihe.
An IHE Integration Statement is not intended to promote or advertise aspects of a product not directly related to its implementation of IHE capabilities.
Format of an IHE Integration Statement
Each Integration Statement shall follow the format shown below. Vendors may add a cover page and any necessary additional information in accordance with their product documentation policies.
| IHE Integration Statement | Date | 12 Oct 2005 |
| Vendor | Product Name | Version |
| Any Medical Systems Co. | IntegrateRecord | V2.3 |
| This product implements all transactions required in the IHE Technical Framework to support the IHE Integration Profiles, Actors and Options listed below: | ||
| Integration Profiles Implemented | Actors Implemented | Options Implemented |
| Cross-Enterprise Sharing of Medical Summaries | Document Consumer | View Option |
| Audit Trail and Node Authentication | Secure Node | none |
| Patient Identity Cross-referencing | Patient Identifier Cross-reference Consumer | PIX Update Notification |
| Internet address for vendor's IHE information:www.anymedicalsystemsco.com/ihe | ||
| Links to Standards Conformance Statements for the Implementation | ||
| HL7 | www.anymedicalsystemsco.com/hl7 | |
| Links to general information on IHE | ||
| In North America: www.ihe.het | In Europe: www.ihe-europe.org | In Japan: www.jira-net.or.jp/ihe-j |
IHE Integration Statement template
An IHE Integration Statement template (MS Word version) is available here.
The IHE Product Registry
The assumption of an integration statement is that all actors listed are functionally grouped and conform to any profile specifications for such groupings. In case of exceptions the vendor must explicitly describe the functional groupings.
IHE has developed a new Web-based database of Integration Statements. The IHE Product Registry enables developers to create, manage and publish Integration Statements for their commercial and open source healthcare IT systems. It allows users to browse for these systems based on their conformance with specific IHE Actors and Profiles. The system is open for use by developers and users now!
Appendix D - Braden Scale for Predicting Pressure Sore Risk
See File:Braden.pdf
Glossary
The following terms are used in various places within this technical framework, and are defined below. The complete IHE Glossary is available on the IHE Wiki at http://wiki.ihe.net/index.php/IHE_Glossary .
- Actor
- An entity within a use case diagram that can perform an action within a use case diagram. Possible actions are creation or consumption of a message
- Acuity Assessment
Also known as triage category, this is the acuity of the patient assigned during the process of ED triage. A number of evidenced based triage scales exist, including the Emergency Severity Index (ESI), Canadian Triage and Acuity Scale (CTAS), the Australasian Triage Scale (ATS), and the Manchester Triage System. In many emergency departments, patients may simply be classified as emergent, urgent or non-urgent.
- ADT
- Admit, Discharge & Transfer.
- Affinity Domain Policy
- Affinity Domain Policy that clearly defines the appropriate uses of the XDS Affinity Domain. Within this policy is a defined set of acceptable use Privacy Consent Policies that are published and understood.
- ASTM
- Formerly the American Society of Testing and Materials, now ASTM International. An SDO that develops a number of standards across a wide variety of industries, including healthcare.
- ATNA
- Audit Trail and Node Authentication. An IHE ITI profile.
- Care Context
- The participations surrounding the care provision act, and the attributes of that act. Everything in the document header. Data history, links to clinical reasoning.
- Continuity of Care Document(CCD)
- An HL7 Clinical Document Architecture (CDA) implementation alternative to ASTM ADJE2369 for institutions or organizations committed to HL7 standards. This specification was developed as a collaborative effort between ASTM and HL7. More information is available from http://www.hl7.org.
- Continuity of Care Record (CCR)
- A core data set of the most relevant administrative, demographic, and clinical information facts about a patient’s healthcare, covering one or more encounters. The CCR is Designation E2369-05 of the ASTM (American Society for Testing and Materials, International). More information is available from http://www.astm.org.
- Clinical Document Architecture (CDA)
- An HL7 standard for the exchange for clinical documents. It specifies the structure and semantics of clinical documents. More information is available from http://www.hl7.org.
- Content Binding
- A content binding describes how the payload used in an IHE transaction is related to and/or constrained by the data elements contained within the content sent or received in those transactions.
- CRS
- Care Record Summary. An implementation guide that constrains CDA Release 2 for Care Record Summary documents.
- CT
- Consistent Time Integration Profile.
- DICOM
- Digital Imaging and Communication in Medicine
- DSG
- Digital Signatures. An IHE ITI Profile.
- EDIS
- An Emergency Department Information System (EDIS) is an extended EHR system used to manage data in support of Emergency Department patient care and operations. The functions of an EDIS may be provided by a single application or multiple applications.
- eMPI
- Enterprise Master Patient Index.
- EMR
- Electronic Medical Record, an Electronic Health Record system used within an enterprise to deliver care (also called EHR-CR by IHE-XDS).
- Estimated Time of Arrival
- the time the patient being referred can be expected to arrive in the emergency department.
- EUA
- Enterprise User Authentication Integration Profile.
- Expected Actions
- Actions which should occur as the result of a trigger event.
- HIMSS
- Healthcare Information and Management Systems Society.
- HL7
- Health Level Seven
- HIS
- Hospital Information System.
- IHE
- Integrating the Healthcare Enterprise.
- Interaction Diagram
- A diagram that depicts data flow and sequencing of events.
- IT
- Information Technology.
- Logical Observation Identifiers Names and Codes (LOINC®)
- A vocabulary developed by the Regenstrief Institute aimed at standardizing laboratory and clinical codes for use in clinical care, outcomes management, and research. Additional information found at http://www.regenstrief.org/medinformatics/loinc/.
- Mode of Arrival
- The method of transportation used to transport the patient to the Emergency Department.
- MPI
- Master Patient Index.
- MRN
- Medical Record Number.
- NAV
- Notification of Document Availability
- OID
- Object Identifier. (See also 'Globally Unique Identifier').
- Patient Identifier Cross-reference Domain
- Consists of a set of Patient Identifier Domains known and managed by a Patient Identifier Cross-reference Manager Actor. The Patient Identifier Cross-reference Manager Actor is responsible for providing lists of "alias" identifiers from different Patient Identifier Domains.
- Patient Identifier Domain
- A single system or a set of interconnected systems that all share a common identification scheme for patients. Such a scheme includes: (1) a single identifier-issuing authority, (2) an assignment process of an identifier to a patient, (3) a permanent record of issued patient identifiers with associated traits, and (4) a maintenance process over time. The goal of Patient Identification is to reduce errors.
- Portable Document Format.
- PIX
- Patient Identifier Cross Referencing. An IHE ITI Profile.
- PDQ
- Patient Demographics Query. An IHE ITI Profile.
- PHR
- Personal Health Record
- Procedure
- In the context of a "Pre-procedure History and Physical," the "procedure" is a surgery or an invasive examination of a patient that is required by quality review organizations to be preceded by a pre-procedure assessment of procedure risk and anesthesia risk. This assessment is typically referred to as a "Pre-operative" or "Pre-procedure History and Physical."
- Process Flow Diagram
- A graphical illustration of the flow of processes and interactions among the actors involved in a particular example.
- Proposed disposition
- the intended disposition (i.e. admission to ICU, discharge to home, transfer to psychiatric hospital), if known, that the referring provider expects the patient will end up after the emergency department intervention.
- Referral Source
- An individual, group, or agency that determined the patient should seek care at the ED. Referral source may be used to determine appropriate discharge referrals and services, or to provide surveillance data for program and service planning, or to examine referral patterns.
- Role
- The actions of an actor in a use case.
- RSNA
- Radiological Society of North America.
- sig.
- A Latin abbreviation for signetur used to represent the instruction following the medication name.
- Scope
- A brief description of the transaction.
SNOMED-CT® A comprehensive clinical terminology, originally created by the College of American Pathologists (CAP) and, as of April 2007, owned, maintained, and distributed by the International Health Terminology Standards Development Organisation (IHTSDO), a non-for-profit association in Denmark. The CAP continues to support SNOMED CT operations under contract to the IHTSDO and provides SNOMED-related products and services as a licensee of the terminology. More information available from http://www.ihtsdo.org/ or the United States National Library of Medicine at http://www.nlm.nih.gov/research/umls/Snomed/snomed_main.html
- Transport Mode
- the method the patient employs, or is provided to get to the emergency department.
- Trigger Event
- An event such as the reception of a message or completion of a process, which causes another action to occur.
- UID
- Unique Identifier (See also Globally Unique Identifier).
- Universal ID
- Unique identifier over time within the UID type. Each UID must belong to one of specifically enumerated species. Universal ID must follow syntactic rules of its scheme.
- Use Case
- A graphical depiction of the actors and operation of a system.
- XUA
- Cross Enterprise User Authentication
- XDS
- Cross Enterprise Document Sharing
Volume 2
HIMSS and RSNA
Integrating the Healthcare Enterprise
IHE Patient Care Coordination
Technical Framework
Basic Patient Privacy Consents
Volume 2
Revision 2.0
2006-2007
Draft
HIMSS and RSNA
Integrating the Healthcare Enterprise
IHE Patient Care Coordination
Technical Framework
Volume II
Revision 3.0
2008-2009
Public Comment
- (PCC TF-2/Preface)Preface
- (PCC TF-2/Introduction)Introduction
IHE Transactions
This section defines each IHE transaction in detail, specifying the standards used, and the information transferred.
Cross Enterprise Document Content Transactions
At present, all transactions used by the PCC Content Profiles appear in ITI TF-2. General Options defined in content profiles for a Content Consumer are described below.
View Option
A Content Consumer that supports the View Option shall be able to:
- Use the appropriate XD* transactions to obtain the document along with associated necessary metadata.
- Render the document for viewing. This rendering shall meet the requirements defined for CDA Release 2 content presentation semantics (See Section 1.2.4 of the CDA Specification: Human readability and rendering CDA Documents). CDA Header information providing context critical information shall also be rendered in a human readable manner. This includes at a minimum the ability to render the document with the stylesheet specifications provided by the document source, if the document source provides a stylesheet. Content Consumers may optionally view the document with their own stylesheet, but must provide a mechanism to view using the source stylesheet.
- Support traversal of links for documents that contain links to other documents managed within the sharing framework.
- Print the document to paper.
Document Import Option
This Option requires that the View Option be supported. In addition, the Content Consumer that supports the Document Import Option shall be able to support the storage of the entire document (as provided by the sharing framework, along with sufficient metadata to ensure its later viewing) both for discharge summary or referral documents. This Option requires the proper tracking of the document origin. Once a document has been imported, the Content Consumer shall offer a means to view the document without the need to retrieve it again from the sharing framework. When viewed after it was imported, a Content Consumer may chose to access the sharing framework to find out if the related Document viewed has been deprecated, replaced or addended.
| Note: | For example, when using XDS, a Content Consumer may choose to query the Document Registry about a document previously imported in order to find out if this previously imported document may have been replaced or has received an addendum. This capability is offered to Content Consumers by this Integration Profile, but not required, as the events that may justify such a query are extremely implementation specific. |
Section Import Option
This Option requires that the View Option be supported. In addition, the Content Consumer that supports the Section Import Option shall be able to support the import of one or more sections of the document (along with sufficient metadata to link the data to its source) both for discharge summary or referral. This Option requires the proper tracking of the document section origin. Once sections have been selected, a Content Consumer shall offer a means to copy the imported section(s) into local data structures as free text. This is to support the display of section level information for comparison or editing in workflows such as medication reconciliation while discrete data import is not possible. When viewed again after it is imported, a Content Consumer may chose to access the sharing framework to find out if the related information has been updated.
| Note: | For example, when using XDS, a Content Consumer may choose to query the Document Registry about a document whose sections were previously imported in order to find out if this previously imported document may have been replaced or has received an addendum. This capability is offered to Content Consumers by this Integration Profile, but not required, as the events that may justify such a query are extremely implementation specific. |
This Option does not require, but does not exclude the Content Consumer from offering a means to select and import specific subsets of the narrative text of a section.
Discrete Data Import Option
This Option does not require that the View, Import Document or Section Import Options be supported. The Content Consumer that supports the Discrete Data Import Option shall be able to support the storage of the structured content of one or more sections of the document. This Option requires that the user be offered the possibility to select among the specific sections that include structured content a set of clinically relevant record entries (e.g. a problem or an allergy in a list) for import as part of the local patient record with the proper tracking of its origin.
| Note: | The Discrete Data Import Option does not require the support of the View, Import Document or Import Sections Options so that it could be used alone to support implementations of Content Consumers such as Public Health Data or Clinical Research systems that might aggregate and anonymize specific population healthcare information data as Document Consumer Actors, but one where no care provider actually views the medical summaries. |
When discrete data is accessed after it was imported, a Content Consumer may choose to check if the document related to the discrete data viewed has been deprecated, replaced or addended.
A Content Consumer Actor grouped with the XDS Document Source Actor may query the Document Registry about a document from which discrete data was previously imported in order to find out if this previously imported document may have been replaced or has received an addendum. This capability is offered to Content Consumers by this Integration Profile, but not required, as the events that may justify such a query are extremely implementation specific.
IHE Patient Care Coordination Bindings
This section describes how the payload used in a transaction of an IHE profile is related to and/or constrains the data elements sent or received in those transactions. This section is where any specific dependencies between the content and transaction are defined.
A content integration profile can define multiple bindings. Each binding should identify the transactions and content to which it applies.
The source for all required and optional attributes have been defined in the bindings below. Three tables describe the three main XDS object types: XDSDocumentEntry, XDSSubmissionSet, and XDSFolder. XDSSubmissionSet and XDSDocumentEntry are required. Use of XDSFolder is optional. These concepts are universal to XDS, XDR and XDM.
The columns of the following tables are:
- <XXX> attribute – name of an XDS attribute, followed by any discussion of the binding detail.
- Optional? - Indicates the required status of the XDS attribute, and is one of R, R2, or O (optional). This column is filled with the values specified in the XDS Profile as a convenience.
- Source Type – Will contain one of the following values:
| Source Type | Description |
| SA | Source document Attribute – value is copied directly from source document. The Source/Value column identifies where in the source document this attribute comes from. Specify the location in XPath when possible. |
| SAT | Source document Attribute with Transformation – value is copied from source document and transformed. The Source/Value column identifies where in the source document this attribute comes from. Specify the location in XPath when possible. Extended Discussion column must not be empty and the transform must be defined in the extended discussion |
| FM | Fixed (constant) by Mapping - for all source documents. Source/Value column contains the value to be used in all documents. |
| FAD | Fixed by Affinity Domain – value configured into Affinity Domain, all documents will use this value. |
| CAD | Coded in Affinity Domain – a list of acceptable codes are to be configured into Affinity Domain. The value for this attribute shall be taken from this list. |
| CADT | Coded in Affinity Domain with Transform - a list of acceptable codes are to be configured into Affinity Domain. The value for this attribute shall be taken from this list. |
| n/a | Not Applicable – may be used with an optionality R2 or O attribute to indicate it is not to be used. |
| DS | Document Source – value comes from the Document Source actor. Use Source/Value column or Extended Discussion to give details. |
| O | Other – Extended Discussion must be 'yes' and details given in an Extended Discussion. |
- Source/Value – This column indicates the source or the value used.
The following tables are intended to be summaries of the mapping and transforms. The accompanying sections labeled 'Extended Discussion' are to contain the details as necessary.
Medical Document Binding to XDS, XDM and XDR
This binding defines a transformation that generates metadata for the XDSDocumentEntry element of appropriate transactions from the XDS, XDM and XDR profiles given a medical document and information from other sources. The medical document refers to the document being stored in a repository that will be referenced in the registry. The other sources of information include the configuration of the Document Source actor, the Affinity Domain, the site or facility, local agreements, other documents in the registry/repository, and this Content Profile.
In many cases, the CDA document is created for the purposes of sharing within an affinity domain. In these cases the context of the CDA and the context of the affinity domain are the same, in which case the following mappings shall apply.
In other cases, the CDA document may have been created for internal use, and are subsequentyly being shared. In these cases the context of the CDA document would not neccessarily coincide with that of the affinity domain, and the mappings below would not necessarily apply.
Please note the specifics given in the table below.
XDSDocumentEntry Metadata
| XDSDocumentEntry Attribute | Optional? | Source Type | Source/ Value |
|---|---|---|---|
| availabilityStatus | R | DS | |
| authorInstitution | R2 | SAT |
$inst <=
/ClinicalDocument/author |
| authorPerson | R2 | SAT |
$person <= /ClinicalDocument/author
|
| authorRole | R2 | SAT | This metadata element should be based on a mapping of the participation function defined in the CDA document to the set of author roles configured for the affinity domain. If the context of the CDA coincides with that of the affinity domain, then the following x-path may be appropriate: /ClincicalDocument/author/ participationFunction |
| authorSpecialty | R2 | SAT | This metadata element should be based on a mapping of the code associated with the assignedAuthor to detailed defined classification system for healthcare providers such configured in the affinitity domain. Possible classifications include those found in SNOMED-CT, or the HIPAA Healthcare Provider Taxonomy. If the context of the CDA coincides with that of the affinity domain, then the following x-path may be appropriate: /ClinicalDocument/author/ assignedAuthor/code |
| classCode | R | CADT | Derived from a mapping of /ClinicalDocument/code/@code to an Affinity Domain specified coded value to use and coding system. Affinity Domains are encouraged to use the appropriate value for Type of Service, based on the LOINC Type of Service (see Page 53 of the LOINC User's Manual). Must be consistent with /ClinicalDocument/code/@code |
| classCodeDisplayName | R | CADT | DisplayName of the classCode derived. Derived from a mapping of /ClinicalDocument/code/@code to the appropriate Display Name based on the Type of Service. Must be Consitent with /ClinicalDocument/code/@code |
| confidentialityCode | R | CADT | Derived from a mapping of /ClinicalDocument/confidentialityCode/@code to an Affinity Domain specified coded value and coding system. When using the BPPC profile, the confidentialyCode may also be obtained from the <authorization> element.
|
| comments | O | DS | |
| creationTime | R | SAT | /ClinicalDocument/effectiveTime
|
| entryUUID | R | DS | |
| eventCodeList | O | CADT | These values express a collection of keywords that may be relevant to the consumer of the documents in the registry. They may come from anywhere in the CDA document, according to its purpose. |
| eventCodeDisplayNameList | R (if event Code is valued) |
CADT | These are the display names for the collection of keywords described above. |
| formatCode | R | FM | The format code for each PCC Document content profile is provided within the document specifications. |
| healthcareFacilityTypeCode | R | CAD | A fixed value assigned to the Document Source and configured form a set of Affinity Domain defined values. Must be concistent with /clinicalDocument/code |
| healthcareFacility TypeCodeDisplay Name |
R | CAD | Must be concistent with /clinicalDocument/code |
| intendedRecipient (for XDR, XDM) | O | SAT |
$person <=
/ClinicalDocument/intendedRecipient
"^^^^^&", |
| languageCode | R | SA | /ClinicalDocument/languageCode |
| legalAuthenticator | O | SAT | $person <= /ClinicalDocument/ legalAuthenticator
|
| mimeType | R | FM | text/xml |
| parentDocumentRelationship | R (when applicable) |
DS | Local document versions need not always be published, and so no exact mapping can be determined from the content of the CDA document. The parentDocumentRelationship may be determined in some configurations from the relatedDocument element present in the CDA dsocument. If the context of the CDA coincides with that of the affinity domain, then the following x-path may be appropriate: /ClinicalDocument/relatedDocument/@typeCode |
| parentDocumentId | R (when parent Document Relationship is present) |
DS | Local document versions need not always be published, and so no exact mapping can be determined from the content of the CDA document. The parentDocumentId may be determined in some configurations from the relatedDocument element present in the CDA dsocument. If the context of the CDA coincides with that of the affinity domain, then the following x-path may be appropriate: $docID <= /ClinicalDocument/ relatedDocument/parentDocument/id
|
| patientId | R | DS | The XDS Affinity Domain patient ID can be mapped from the patientRole/id element using transactions from the ITI PIX or PDQ profiles. See sourcePatientId below. If the context of the CDA coincides with that of the affinity domain, then the following x-path may be appropriate:
|
| practiceSettingCode | R | CAD | This elements should be based on a coarse classification system for the class of specialty practice. Recommend the use of the classification system for Practice Setting, such as that described by the Subject Matter Domain in LOINC. |
| practiceSettingCodeDisplayName | R | CAD | This element shall contain the display names associated with the codes described above. |
| serviceStartTime | R2 | SAT | /ClinicalDocument/documentationOf/ serviceEvent/effectiveTime/low/ @value
|
| serviceStopTime | R2 | SAT | /ClinicalDocument/documentationOf/ serviceEvent/effectiveTime/high/ @value
|
| sourcePatientId | R | SAT | $patID <= /ClinicalDocument/recordTarget/ patientRole/id
|
| sourcePatientInfo | R | SAT | /ClinicalDocument/recordTarget/ patientRole
|
| title | O | SA | /ClinicalDocument/title |
| typeCode | R | CADT | /ClinicalDocument/code/@code
|
| typeCodeDisplay Name |
R | CADT | /ClinicalDocument/code/@displayName |
| uniqueId | R | SAT | $docID <= /ClinicalDocument/id
|
XDSSubmissionSet Metadata
The submission set metadata is as defined for XDS, and is not necessarily affected by the content of the clinical document. Metadata values in an XDSSubmissionSet with names identical to those in the XDSDocumentEntry may be inherited from XDSDocumentEntry metadata, but this is left to affinity domain policy and/or application configuration.
Use of XDS Submission Set
This content format uses the XDS Submission Set to create a package of information to send from one provider to another. All documents referenced by the Medical Summary in this Package must be in the submission set.
Use of XDS Folders
No specific requirements identified.
Configuration
IHE Content Profiles using this binding require that Content Creators and Content Consumers be configurable with institution and other specific attributes or parameters. Implementers should be aware of these requirements to make such attributes easily configurable. There shall be a mechanism for the publishing and distribution of style sheets used to view clinical documents.
Extensions from other Domains
Scanned Documents (XDS-SD)
XDS-SD is a CDA R2 document and thus conforms to the XDS Metadata requirements in the PCC-TF, volume 2, Section 5 unless otherwise specified below.
XDSDocumentEntry
XDS-SD leverages the XDS DocumentEntry Metadata requirements in the PCC-TF, volume 2, Section 5.1.1.1.1 and in PCC_TF-2/Bindings unless otherwise specified below
XDSDocumentEntry.formatCode
The XDSDocumentEntry.formatCode shall be urn:ihe:iti:xds-sd:pdf:2008 when the document is scanned pdf and urn:ihe:iti:xds-sd:text:2008 when the document is scanned text. The formatCode codeSystem shall be 1.3.6.1.4.1.19376.1.2.3.
XDSDocumentEntry.uniqueId
This value shall be the ClinicalDocument/id in the HL7 CDA R2 header. The root attribute is required, and the extension attribute is optional. In accordance with the XDS.a profile, total length is limited to 128 characters; for XDS.b the limit is 256 characters. Additionally see PCC-TF, volume 2, Section 5.1.1.1.1 or PCC_TF-2/Bindings for further content specification.
Relating instances of XDS-SD documents
In general, most instances of XDS-SD will not have parent documents. It is possible, however, in some specific use cases that instances of XDS-SD documents are related. For example, for a particular document it may be the case that both the PDF scanned content and somewhat equivalent plaintext need to be wrapped and submitted. Each document would correspond to separate XDSDocumentEntries linked via an XFRM Association that indicates one document is a transform of the other. These can be submitted in a single submission set, or in separate ones. Other specific examples may exist and this profile does not preclude the notion of a parent document for these cases.
XDSSubmissionSet
No additional constraints. Particular to this profile, a legitimate use of submission sets would be to maintain a logical grouping of multiple XDS-SD documents. We encourage such usage. For more information, see PCC-TF-2 Section 5.1.1.1.2 or PCC_TF-2/Bindings.
XDSFolder
No additional requirements. For more information, see PCC-TF-2 Section 5.1.1.1.3 or PCC_TF-2/Bindings.
Basic Patient Privacy Consents (BPPC)
Laboratory Reports (XD-LAB)
XD-Lab is a CDA R2 document and thus conforms to the XDS Metadata requirements in the PCC-TF, volume 2, Section 5 unless otherwise specified below.
XDSDocumentEntry
XD-Lab leverages the XDS DocumentEntry Metadata requirements in the PCC-TF, volume 2, Section 5.1.1.1.1 and in PCC_TF-2/Bindings unless otherwise specified below
XDSDocumentEntry.eventCodeList
XD-Lab documents further constrain the the XDSDocumentEntry.eventCodeList to the following.
| Attribute | Optional? | Source Type | Source/ Value |
|---|---|---|---|
| eventCodeList | R2 | SAT | ClinicalDocument / component / structuredBody / component / section / entry / act / entryRelationship / organizer (templateId="1.3.6.1.4.1.19376.1.3.1.1")/ component / observation(templateId="1.3.6.1.4.1.19376.1.3.1.1.1")/code
AND ClinicalDocument / component / structuredBody / component / section / entry / act / subject / code If the document has Reportable Condition, then this code shall be among those listed in the eventCodeList. Additionally, if the document contains information about a Non-Human Subject, then the code that indicates what this subject is shall be among those listed in the eventCodeList. Thus, this attribute has been enhanced from the XDS profile from O to R2. |
XDSDocumentEntry.formatCode
The XDSDocumentEntry.formatCode shall be urn:ihe:lab:xd-lab:2008 The formatCode codeSystem shall be 1.3.6.1.4.1.19376.1.2.3.
XDSSubmissionSet
No additional constraints. For more information, see PCC-TF-2 Section 5.1.1.1.2 or PCC_TF-2/Bindings.
XDSFolder
No additional requirements. For more information, see PCC-TF-2 Section 5.1.1.1.3 or PCC_TF-2/Bindings.
Namespaces and Vocabularies
This section lists the namespaces and identifiers defined or referenced by the IHE PCC Technical Framework, and the vocabularies defined or referenced herein.
The following vocabularies are referenced in this document. An extensive list of registered vocabularies can be found at http://www.hl7.org/oid/.
| codeSystem | codeSystemName | Description |
| 1.3.6.1.4.1.19376.1.5.3.1 | IHE PCC Template Identifiers | This is the root OID for all IHE PCC Templates. A list of PCC templates can be found below in CDA Release 2.0 Content Modules. |
| 1.3.6.1.4.1.19376.1.5.3.2 | IHEActCode | See IHEActCode Vocabulary below |
| 1.3.6.1.4.1.19376.1.5.3.3 | IHE PCC RoleCode | See IHERoleCode Vocabulary below |
| 1.3.6.1.4.1.19376.1.5.3.4 | Namespace OID used for IHE Extensions to CDA Release 2.0 | |
| 2.16.840.1.113883.10.20.1 | CCD Root OID | Root OID used for by ASTM/HL7 Continuity of Care Document |
| 2.16.840.1.113883.5.112 | RouteOfAdministration | See the HL7 RouteOfAdministration Vocabulary |
| 2.16.840.1.113883.5.1063 | SeverityObservation | See the HL7 SeverityObservation Vocabulary |
| 2.16.840.1.113883.5.7 | ActPriority | See the HL7 ActPriority Vocabulary |
| 2.16.840.1.113883.6.1 | LOINC | Logical Observation Identifier Names and Codes |
| 2.16.840.1.113883.6.96 | SNOMED-CT | SNOMED Controlled Terminology |
| 2.16.840.1.113883.6.103 | ICD-9CM (diagnosis codes) | International Classification of Diseases, Clinical Modifiers, Version 9 |
| 2.16.840.1.113883.6.104 | ICD-9CM (procedure codes) | International Classification of Diseases, Clinical Modifiers, Version 9 |
| 2.16.840.1.113883.6.26 | MEDCIN | A classification system from MEDICOMP Systems. |
| 2.16.840.1.113883.6.88 | RxNorm | RxNorm |
| 2.16.840.1.113883.6.63 | FDDC | First DataBank Drug Codes |
| 2.16.840.1.113883.6.12 | C4 | Current Procedure Terminology 4 (CPT-4) codes. |
| 2.16.840.1.113883.6.257 | Minimum Data Set for Long Term Care | The root OID for Minimum Data Set Answer Lists |
| 1.2.840.10008.2.16.4 | DCM | DICOM Controlled Terminology; PS 3.16 Content Mapping Resource, Annex D |
| 2.16.840.1.113883.6.24 | MDC | ISO/IEEE 11073 Medical Device Nomenclature |
| 2.16.840.1.113883.3.26.1.5 | NDF-RT | National Drug File Reference Terminology (NCI version) |
| 2.16.840.1.113883.11.19465 | nuccProviderCodes | National Uniform Codes Council Healthcare Provider Terminology |
| 2.16.840.1.113883.6.255.1336 | X12DE1336 | Insurance Type Code (ASC X12 Data Element 1336) |
| 2.16.840.1.113883.6.256 | RadLex | RadLex (Radiological Society of North America) |
The IHE FormatCode vocabulary is now managed in an Implementation Guide published using FHIR.
- formal canonical URI https://profiles.ihe.net/fhir/ihe.formatcode.fhir/ValueSet-formatcode.html
- formal publication URL https://profiles.ihe.net/fhir/ihe.formatcode.fhir/
- FormatCode gitHub repository for source of the Implementation Guide can be used to register issues, or create pull requests for modifications. Formal governance is managed by ITI Technical Committee.
This FormatCode vocabulary represents:
- Code System 1.3.6.1.4.1.19376.1.2.3
- Value Set 1.3.6.1.4.1.19376.1.2.7.1
IHEActCode Vocabulary
| CCD | ASTM/HL7 Continuity of Care Document | |
| CCR | ASTM CCR Implementation Guide |
The IHEActCode vocabulary is a small vocabulary of clinical acts that are not presently supported by the HL7 ActCode vocabulary. The root namespace (OID) for this vocabulary is 1.3.6.1.4.1.19376.1.5.3.2. These vocabulary terms are based on the vocabulary and concepts used in the CCR and CCD standards listed above.
| Code | Description |
| COMMENT | This is the act of commenting on another act. |
| PINSTRUCT | This is the act of providing instructions to a patient regarding the use of medication. |
| FINSTRUCT | This is the act of providing instructions to the supplier regarding the fulfillment of the medication order. |
| IMMUNIZ | The act of immunization of a patient using a particular substance or class of substances identified using a specified vocabulary. Use of this vocabulary term requires the use of either the SUBSTANCE or SUBSTCLASS qualifier described below, along with an identified substance or class of substances. |
| DRUG | The act of treating a patient with a particular substance or class of substances identified using a specified vocabulary. Use of this vocabulary term requires the use of either the SUBSTANCE or SUBSTCLASS qualifier described below, along with an identified substance or class of substances. |
| INTOL | An observation that a patient is somehow intollerant of (e.g., allergic to) a particular substance or class of substances using a specified vocabulary. Use of this vocabulary term requires the use of either the SUBSTANCE or SUBSTCLASS qualifier described below, along with an identified substance or class of substances. |
| SUBSTANCE | A qualifier that identifies the substance used to treat a patient in an immunization or drug treatment act. The substance is expected to be identified using a vocabulary such as RxNORM, SNOMED CT or other similar vocabulary and should be specific enough to identify the ingredients of the substance used. |
| SUBSTCLASS | A qualifier that identifies the class of substance used to treat a patient in an immunization or drug treatment act. The class of substances is expected to be identified using a vocabulary such as NDF-RT, SNOMED CT or other similar vocabulary, and should be broad enough to classify substances by mechanism of action (e.g., Beta Blocker), intended effect (Dieuretic, antibiotic) or ... |
| For Public Comment | What else needs to appear above for SUBSTCLASS? |
IHERoleCode Vocabulary
The IHERoleCode vocabulary is a small vocabulary of role codes that are not presently supported by the HL7 Role Code vocabulary. The root namespace (OID) for this vocabulary is 1.3.6.1.4.1.19376.1.5.3.3.
| Code | Description |
| EMPLOYER | The employer of a person. |
| SCHOOL | The school in which a person is enrolled. |
| AFFILIATED | An organization with which a person is affiliated (e.g., a volunteer organization). |
| PHARMACY | The pharmacy a person uses. |
Folder Content Modules
This section contains modules that describe the content requirements of XDS Folders. At present, the IHE PCC Technical Framework has not defined any Folder Modules.
CDA Release 2.0 Content Modules
This section contains content modules based upon the HL7 CDA Release 2.0 Standard, and related standards and/or implementation guides.
CDA Document Content Modules
Development Only
The PCC Wiki Content is used only for development of IHE PCC Content. The Normative content of the PCC Technical Framework and the current supplements can be found at http://www.ihe.net/Technical_Framework/index.cfm#PCC
 Medical Documents Specification 1.3.6.1.4.1.19376.1.5.3.1.1.1
Medical Documents Specification 1.3.6.1.4.1.19376.1.5.3.1.1.1
This section defines the base set of constraints used by almost all medical document profiles described the PCC Technical Framework.
Standards
| CDAR2 | HL7 CDA Release 2.0 |
| CDTHP | CDA for Common Document Types History and Physical Notes (DSTU) |
| XMLXSL | Associating Style Sheets with XML documents |
Conformance
CDA Release 2.0 documents that conform to the requirements of this content module shall indicate their conformance by the inclusion of the appropriate <templateId> elements in the header of the document. This is shown in the sample document below.
<ClinicalDocument xmlns='urn:hl7-org:v3'> <typeId extension="POCD_HD000040" root="2.16.840.1.113883.1.3"/> <templateId root='1.3.6.1.4.1.19376.1.5.3.1.1.1'/> <id root=' ' extension=' '/> <code code=' ' displayName=' ' codeSystem='2.16.840.1.113883.6.1' codeSystemName='LOINC'/> <title>Medical Documents</title> <effectiveTime value='20240503012005'/> <confidentialityCode code='N' displayName='Normal' codeSystem='2.16.840.1.113883.5.25' codeSystemName='Confidentiality' /> <languageCode code='en-US'/> : <component><structuredBody> </structuredBody></component> </ClinicalDocument> |
<!-- Verify the document type code -->
<assert test='cda:code[@code = "{{{LOINC}}}"]'>
Error: The document type code of a Medical Documents must be {{{LOINC}}}
</assert>
<assert test='cda:code[@codeSystem = "2.16.840.1.113883.6.1"]'>
Error: The document type code must come from the LOINC code
system (2.16.840.1.113883.6.1).
</assert>
Specification
The constraints for encoding of the CDA Header (Level 1) can be found in the CDA for Common Document Types History and Physical Implementation Guide, in the section 2. CDA Header -- General Constraints.
- IHE Medical Documents shall follow all constraints found in that section with the exception of the constraint on realmcode found in CONF-HP-15:.
- IHE Medical Documents which are implemented for the US Realm shall follow ALL constraints found in that section, and shall use both the IHE Medical Document templateId (1.3.6.1.4.1.19376.1.5.3.1.1.1) and the HL7 General Header Constraints templateId (2.16.840.1.113883.10.20.3).}}
| Realm | Constraints | Template IDs Required |
|---|---|---|
| Universal | CONF-HP-1 through CONF-HP-14 CONF-HP-16 through CONF-HP-52 |
1.3.6.1.4.1.19376.1.5.3.1.1.1 |
| US | CONF-HP-1 through CONF-HP-52 | 1.3.6.1.4.1.19376.1.5.3.1.1.1 2.16.840.1.113883.10.20.3 |
Style Sheets
Document sources should provide an XML style sheet to render the content of the Medical Summary document. The output of this style sheet shall be an XHTML Basic (see http://www.w3.org/TR/xhtml-basic/) document that renders the clinical content of a Medical Summary Document as closely as possible as the sending provider viewed the completed document. When a style sheet is provided, at least one processing instruction shall be included in the document that including a link to the URL for the XML style sheet. To ensure that the style sheet is available to all receivers, more than one stylesheet link may be included.
When a stylesheet is used within an XDS Affinity domain, the link to it shall be provided using an HTTPS or HTTP URL.
<?xml-stylesheet href='https://foobar:8080/mystylesheet.xsl' type='text/xsl'?>
When using XDM or XDR to exchange documents, the stylesheet shall also be exchanged on the media. The link to the stylesheet shall be recorded as a relative URL.
<?xml-stylesheet href='../../stylesheets/mystylesheet.xsl' type='text/xsl'?>
Style sheets should not rely on graphic or other media resources. If graphics other media resources are used, these shall be accessible in the same way as the stylesheet. The Content Creator need not be the provider of the resources (stylesheet or graphcs).
When a Content Creator provides a style sheet, Content Consumers must provide a mechanism to render the document with that style sheet. Content Consumers may view the document with their own style sheet.
To record the stylesheet within a CDA Document that might be used in both an XDS and XDM environment, more than one stylesheet processing instruction is required. In this case, all style sheet processing instructions included must include the alternate='yes' attribute.
<?xml-stylesheet href='https://foobar:8080/mystylesheet.xsl' type='text/xsl' alternate='yes'?> <?xml-stylesheet href='../../stylesheets/mystylesheet.xsl' type='text/xsl' alternate='yes'?>
A Content Consumer that is attempting to render a document using the document supplied stylesheet may use the first style sheet processing instruction for which it is able to obtain the style sheet content, and shall not report any errors if it is able to find at least one stylesheet to render with.
Distinctions of None
Information that is sent must clearly identify distinctions between
- None
- It is known with complete confidence that there are none. Used in the context of problem and medication lists, this indicates that the sender knows that there is no relevant information that can be sent.
- None Known
- None are known at this time, but it is not known with complete confidence than none exist. Used in the context of allergy lists, where essentially, it is impossible to prove the negative that no allergies exist, it is only possible to assert that none have been found to date.
- None Known Did Ask
- None are known at this time, and it is not known with complete confidence than none exist, but the information was requested. Also used in the context of allergy lists, where essentially, it is impossible to prove the negative that no allergies exist, it is only possible to assert that none have been found to date.
- Unknown
- The information is not known, or is otherwise unavailable.
In the context of CDA, sections that are required to be present but have no information should use one of the above phrases where appropriate.
An appropriate machine readable entry shall be present for problems, medications and allergies to indicate the reason that no information. Codes for recording unknown or no information are provided in the section on the Problem, Allergy and Medications Entry.
Development Only
The PCC Wiki Content is used only for development of IHE PCC Content. The Normative content of the PCC Technical Framework and the current supplements can be found at http://www.ihe.net/Technical_Framework/index.cfm#PCC
Consents to share information are documents that contain both a human and machine readable description of how a patient has chosen to share their information.
Format Code
The XDSDocumentEntry format code for this content is urn:ihe:pcc:bppc:2007
Parent Template
This document is an instance of the Medical Document template.
Standards
| CDAR2 | HL7 CDA Release 2.0 |
| XDS-SD | Scanned Documents |
Specification
| Data Element Name | Opt | Template ID |
|---|---|---|
| Consent Service Event At least one, and possibly more than one, consent can be provided within the document. |
R | 1.3.6.1.4.1.19376.1.5.3.1.2.6 |
| Authorization Consents may also be protected under a sharing policity. |
O | 1.3.6.1.4.1.19376.1.5.3.1.2.5 |
Conformance
CDA Release 2.0 documents that conform to the requirements of this content module shall indicate their conformance by the inclusion of the appropriate <templateId> elements in the header of the document. This is shown in the sample document below. A CDA Document may conform to more than one template. This content module inherits from the Medical Document content module, and so must conform to the requirements of that template as well, thus all <templateId> elements shown in the example below shall be included.
<ClinicalDocument xmlns='urn:hl7-org:v3'> <typeId extension="POCD_HD000040" root="2.16.840.1.113883.1.3"/> <templateId root='1.3.6.1.4.1.19376.1.5.3.1.1.1'/> |
Schematron
<pattern name='Template_1.3.6.1.4.1.19376.1.5.3.1.1.7'>
<rule context='*[cda:templateId/@root="1.3.6.1.4.1.19376.1.5.3.1.1.7"]'>
<!-- Verify that the template id is used on the appropriate type of object -->
<assert test='../cda:ClinicalDocument'>
Error: The Consent to Share Information can only be used on Clinical Documents.
</assert>
<!-- Verify that the parent templateId is also present. -->
<assert test='cda:templateId[@root="1.3.6.1.4.1.19376.1.5.3.1.1.1"]'>
Error: The parent template identifier for Consent to Share Information is not present.
</assert>
<!-- Verify the document type code -->
<assert test='cda:code[@code = "{{{LOINC}}}"]'>
Error: The document type code of a Consent to Share Information must be {{{LOINC}}}
</assert>
<assert test='cda:code[@codeSystem = "2.16.840.1.113883.6.1"]'>
Error: The document type code must come from the LOINC code
system (2.16.840.1.113883.6.1).
</assert>
<assert test='.//cda:templateId[@root = "1.3.6.1.4.1.19376.1.5.3.1.2.6"]'>
<!-- Verify that all required data elements are present -->
Error: The Consent to Share Information Document must contain a(n) Consent Service Event Entry.
See http://wiki.ihe.net/index.php?title=1.3.6.1.4.1.19376.1.5.3.1.1.7
</assert>
<assert test='.//cda:templateId[@root = "1.3.6.1.4.1.19376.1.5.3.1.2.5"]'>
<!-- Note any missing optional elements -->
Note: This Consent to Share Information Document does not contain a(n) Authorization Entry.
See http://wiki.ihe.net/index.php?title=1.3.6.1.4.1.19376.1.5.3.1.1.7
</assert>
</rule>
</pattern>
Constraints
A consent shall contain a text description of what the patient consented to, a list of codes indicating the policy(s) agreed to, a time range indicating the effective time of the consent, and shall contain a signature signifying the patient agreement to those policy(s) stated in the text description. Finally, consents may be attested to using an electronic digital signature, conforming to the ITI Digital Signature Profile.
The text description and signature may appear as a scanned image. When the consent contains a scanned image, it shall also conform to the constraints of the ITI Scanned Document profile.
A consent shall have one or more <serviceEvent> elements in the header identifying the policies authorized by the document (see Section 4.2.3.4 of CDAR2). Each <serviceEvent> element indicates informed consent to one and only one XDS Affinity Domain policy. More than one policy may be agreed to within a given consent document.
Consent documents should be attested to by either the patient and/or legal guardian, or a third party assigned by the XDS Affinity Domain or its member organizations. The attestation, if present, should be performed using the ITI Digital Signature profile. The signer may be the patient, or a third party.
Appendix A - Examples Using PCC Content Profiles
Example documents conforming to each profile can be found on the IHE wiki at the following URLs.
| Profile and Content | URL |
|---|---|
| XDS-MS | |
| Referral Summary | XDSMS Example1 |
| Discharge Summary | XDSMS Example1 |
| XPHR | |
| XPHR Content | XPHR Example1 |
| XPHR Update | XPHR Example2 |
| (EDR) ED Referral | EDR Example |
| (APS) Antepartum Summary | APS Example |
| (EDES) | |
| Triage Note | EDES Example1 |
| ED Nursing Note | EDES Example2 |
| Composite Triage and Nursing Note | EDES Example3 |
| ED Physician Note | EDES Example4 |
| (FSA) Functional Status Section | FSA Example |
Appendix B - Validating CDA Documents using the Framework
Many of the constraints specified by the content modules defined in the PCC Technical Framework can be validated automatically by software. Automated validation is a very desirable capability, as it makes it easier for implementers to test the correctness of their implementations. With regard to validation of the content module, the PCC Technical Framework narrative is the authoritative specification, not any automated software tool. Having said that, it is still very easy to create a validation framework for the IHE PCC Technical Framework using a XML validation tool such as Schematron. Since each content module has a name (the template identifier), any XML instance that reports itself to be of that "class" can be validated by creating assertions that must be true for each constraint indicated for the content module. In the XML representation, the <templateId> element is a child of the element that is claiming conformance to the template named. Thus the general pattern of a Schematron that validates a specific template is shown below:
<schema xmlns="http://www.ascc.net/xml/schematron" xmlns:cda="urn:hl7-org:v3">
<ns prefix="cda" uri="urn:hl7-org:v3" />
<pattern name='ReferralSummary'>
<rule context='*[cda:templateId/@root="1.3.6.1.4.1.19376.1.5.3.1.1.3]"'>
<!-- one or more assertions made by the content module -->
</rule>
</pattern>
</schema>
Validating Documents
For document content modules, the pattern can be extended to support common document content module constraints as shown below:
<schema xmlns="http://www.ascc.net/xml/schematron" xmlns:cda="urn:hl7-org:v3">
<ns prefix="cda" uri="urn:hl7-org:v3" />
<pattern name='ReferralSummary'>
<rule context='*[templateId/@root="1.3.6.1.4.1.19376.1.5.3.1.1.3]"'>
<!-- Verify that the template id is used on the appropriate type of object -->
<assert test='../ClinicalDocument'>
Error: The referral content module can only be used on Clinical Documents.
</assert>
<!-- Verify that the parent templateId is also present. -->
<assert test='templateId[@root="1.3.6.1.4.1.19376.1.5.3.1.1.2"]'>
Error: The parent template identifier for medical summary is not present.
</assert>
<!-- Verify the document type code -->
<assert test='code[@code = "34133-9"]'>
Error: The document type code of a referral summary must be
34133-9 SUMMARIZATION OF EPISODE NOTE.
</assert>
<assert test='code[@codeSystem = "2.16.840.1.113883.6.1"]'>
Error: The document type code must come from the LOINC code
system (2.16.840.1.113883.6.1).
</assert>
<!-- Verify that all required data elements are present -->
<assert test='.//templateId[@root = "1.3.6.1.4.1.19376.1.5.3.1.3.1"]'>
Error: A referral summary must contain a reason for referral.
</assert>
<!-- Alert on any missing required if known elements -->
<assert test='.//templateId[@root = "1.3.6.1.4.1.19376.1.5.3.1.3.8"]'>
Warning: A referral summary should contain a list of history of past illnesses.
</assert>
<!-- Note any missing optional elements -->
<assert test='.//templateId[@root = "1.3.6.1.4.1.19376.1.5.3.1.3.18"]'>
Note: This referral summary does not contain the pertinent review of systems.
</assert>
</rule>
</pattern>
</schema>
Validating Sections
The same pattern can be also applied to sections with just a few minor alterations.
<schema xmlns="http://www.ascc.net/xml/schematron" xmlns:cda="urn:hl7-org:v3">
<ns prefix="cda" uri="urn:hl7-org:v3" />
<pattern name='ReasonForReferralUncoded'>
<rule context='*[templateId/@root="1.3.6.1.4.1.19376.1.5.3.1.3.1"]'>
<!-- Verify that the template id is used on the appropriate type of object -->
<assert test='section'>
Error: The coded reason for referral module can only be used on a section.
</assert>
<assert test='false'>
Manual: Manually verify that this section contains narrative providing the
reason for referral.
</assert>
<!-- Verify that the parent templateId is also present. -->
<assert test='templateId[@root="1.3.6.1.4.1.19376.1.5.3.1.3.1"]'>
Error: The parent template identifier for the reason for referral
module is not present.
</assert>
<!-- Verify the section type code -->
<assert test='code[@code = "42349-1"]'>
Error: The section type code of the reason for referral section must be 42349-1
REASON FOR REFERRAL.
</assert>
<assert test='code[@codeSystem = "2.16.840.1.113883.6.1"]'>
Error: The section type code must come from the LOINC code
system (2.16.840.1.113883.6.1).
</assert>
</pattern>
<pattern name='ReasonForReferralCoded'>
<rule context='*[templateId/@root="1.3.6.1.4.1.19376.1.5.3.1.3.2"]'>
<!-- The parent template will have already verified the type of object -->
<!-- Verify that the parent templateId is also present. -->
<assert test='templateId[@root="1.3.6.1.4.1.19376.1.5.3.1.3.1"]'>
Error: The parent template identifier for the reason for referral
module is not present.
</assert>
<!-- Don't bother with the section type code, as the parent template caught it -->
<!-- Verify that all required data elements are present -->
<assert test='.//templateId[@root = "1.3.6.1.4.1.19376.1.5.3.1.4.13"]'>
Error: A coded reason for referral section must contain an simple observation.
</assert>
<!-- Alert on any missing required if known elements -->
<!-- Note any missing optional elements -->
</rule>
</pattern>
</schema>
A similar pattern can also be followed for Entry and Header content modules, and these are left as an exercise for the reader.
Phases of Validation and Types of Errors
Note that each message in the Schematrons shown above start with a simple text string that indicates whether the message indicates one of the following conditions:
- An error, e.g., the failure to transmit a required element,
- A warning, e.g., the failure to transmit a required if known element,
- A note, e.g., the failure to transmit an optional element.
- A manual test, e.g., a reminder to manually verify some piece of content.
Schematron supports the capability to group sets of rules into phases by the pattern name, and to specify which phases of validation should be run during processing. To take advantage of this capability, one simply breaks each <pattern> element above up into separate patterns depending upon whether the assertion indicates an error, warning, note or manual test, and then associate each pattern with a different phase. This is shown in the figure below.
<schema xmlns="http://www.ascc.net/xml/schematron" xmlns:cda="urn:hl7-org:v3">
<ns prefix="cda" uri="urn:hl7-org:v3" />
<phase id="errors">
<active pattern="ReasonForReferralUncoded_Errors"/>
<active pattern="ReasonForReferralCoded_Errors"/>
</phase>
<phase id="manual">
<active pattern="ReasonForReferralUncoded_Manual"/>
</phase>
<pattern name='ReasonForReferralUncoded_Errors'>
<rule context='*[templateId/@root="1.3.6.1.4.1.19376.1.5.3.1.3.1"]'>
<assert test='section'>
Error: The coded reason for referral module can only be used on a section.
</assert>
<assert test='code[@code = "42349-1"]'>
Error: The section type code of the reason for referral section must be 42349-1
REASON FOR REFERRAL.
</assert>
<assert test='code[@codeSystem = "2.16.840.1.113883.6.1"]'>
Error: The section type code must come from the LOINC code
system (2.16.840.1.113883.6.1).
</assert>
</rule>
</pattern>
<pattern name='ReasonForReferralUncoded_Manual'>
<rule context='*[templateId/@root="1.3.6.1.4.1.19376.1.5.3.1.3.1"]'>
<assert test='false'>
Manual: Manually verify that this section contains narrative providing the
reason for referral.
</assert>
</pattern>
<pattern name='ReasonForReferralCoded_Errors'>
<rule context='*[templateId/@root="1.3.6.1.4.1.19376.1.5.3.1.3.2"]'>
<assert test='templateId[@root="1.3.6.1.4.1.19376.1.5.3.1.3.1"]'>
Error: The parent template identifier for the reason for referral not present.
</assert>
<assert test='.//templateId[@root = "1.3.6.1.4.1.19376.1.5.3.1.4.13"]'>
Error: A coded reason for referral section must contain an simple observation.
</assert>
</rule>
</pattern>
</schema>
Using these simple "templates" for template validation one can simply create a collection of Schematron patterns that can be used to validate the content modules in the PCC Technical Framework. Such Schematrons are expected to be made available as part of the MESA test tools that are provided to IHE Connectathon participants, and which will also be made available to the general public after connectathon.
Appendix C - Extensions to CDA Release 2.0
This section describes extensions to CDA Release 2.0 that are used by the IHE Patient Care Coordination Technical Framework.
IHE PCC Extensions
All Extensions to CDA Release 2.0 created by the IHE PCC Technical Committee are in the namespace urn:ihe:pcc:hl7v3.
The approach used to create extension elements created for the PCC Technical Framework is the same as was used for the HL7 Care Record Summary (see Appendix E) and the ASTM/HL7 Continuity of Care Document (see secion 7.2).
replacementOf
The <replacementOf> extension element is applied to a section appearing in a PHR Update Document to indicate that that section's content should replace that of a previously existing section. The identifier of the previously existing section is given so that the PHR Manager receiving the Update content will know which section to replace. The model for this extension is shown below.
Use of this extension is shown below. The <replacementOf> element appears after all other elements within the <section> element. The <id> element appearing in the <externalDocumentSection> element shall provide the identifier of the section being replaced in the parent document.
<section>
<id root=' ' extension=' '/>
|
Extensions Defined Elsewhere used by IHE PCC
Entity Identifiers
There is often a need to record an identifer for an entity so that it can be subsequently referenced. This extension provides a mechnism to store that identifier. The element appears after any <realm>, <typeId> or <templateId> elements, but before all others in the entity where it is used:
<playingEntity classCode='ENT' determinerCode='INSTANCE'> <sdtc:id root='1.3.6.4.1.4.1.2835.2' extension='EntityID'/> : . </playingEntity>
Patient Identifier
There is a need to record the identifer by which a patient is known to another healthcare provider. This extension provides a role link between the assigned, related or associated entity, and the patient role.
Use of this extension to record the identifier under which the patient is known to a provider is shown below.
<assignedEntity>
<id extension='1' root='1.3.6.4.1.4.1.2835.1'/>
|
The <patient> element records the link between the related, assigned or associated entity and the patient. The <id> element provides the identifier for the patient. The root attribute of the <id> should be the namespace used for patient identifiers by the entity. The extension attribute of the <id> element shall be the patient's medical record number or other identifier used by the entity to identify the patient.