Non-patient File Sharing (NPFS)
Non-Patient File Sharing (NPFSm)
Introduction
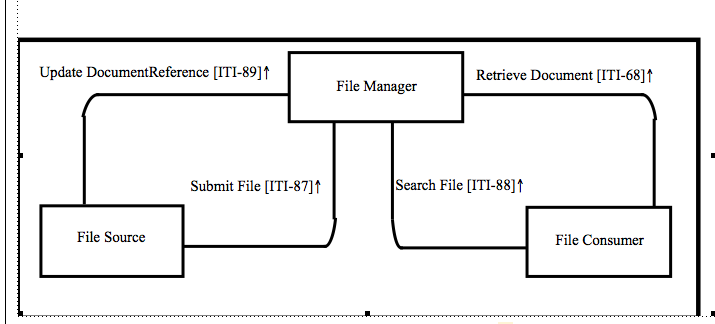
This supplement defines how to enable the sharing of non-patient files. Those files can be created, consumed and updated by many different systems involved in a wide variety of data sharing workflows (clinical workflow definition, domain policies sharing, stylesheets management, etc.). This supplement identifies three actors: File Manager, File Consumer, and File Source. To fulfill use-cases requirements, this profile defines three new transactions (Submit File transaction, Search File transaction and Update DocumentReference transaction) and re-uses an MHD transaction: Retrieve Document [ITI-68]. There are IHE Profiles that manage documents that are not patient-related; this profile does not require that the actors be able to process the contents of the files being shared. Understanding this profile does not require the knowledge of the files shared. The NPFSm Profile specifies transactions for the sharing of files. Any file type can be shared using this profile; however specific guidance is given for three types of files:
- Workflow Definitions: files which define the processing rules for a specific clinical/administrative workflow (see ITI TF-1: 30.4.1.1 “XDW Workflow Architecture” for additional information).
- Privacy Domain Policies: files which describe a specific privacy policy that applies to, or may be agreed by the patient (see ITI TF-1: 19.2 “Creating Patient Privacy Policies” for further details).
- Stylesheets: structured documents used by user-agents (e.g., Web Browsers) to render the content of an XML document.
Local policies may extend the types of files shared using NPFSm and that can be classified using the metadata model described in this profile.
Actors and Transactions
Actors
Authorization Decisions Manager
The Authorization Decisions Manager is responsible for the management of access control decisions in the entire XDS domain. From the Access Control point of view, this actor is the unique Policy Decision Point (PDP) of the entire domain for all documents because it may decide on the outcome of an incoming authorization request in order to provide access to specific resources (documents). The Authorization Decisions Manager completes the Authorization Decision creating and storing a security token. This security token does not need to be exposed to other systems, and it certifies the decision made. This actor could implement additional Access Control functionalities required in the specific implementation scenario. (Refer to the White Paper IHE ITI Access Control White Paper for further information about PDP and Access Control Systems).
Authorization Decisions Verifier
The Authorization Decisions Verifier is the actor that verifies if the Requester Entity is authorized to access specific resources by querying the Authorization Decisions Verifier. This actor enforces the Access Decision made by the trusted Policy Decision Point, so it acts as a Policy Enforcement Point (PEP). This actor enables the secure exposure of documents, allowing access only to Requester Entities previously authorized by the Policy Decision Point. The Requester Entities (XDS Document Consumer) convey at least the following information to the Authorization Decisions Verifier:
- Requester Entity that obtains authorization (e.g., using an identity assertion)
- The unique ID of the document that can be accessed (within the Retrieve Document Set-b Request)
(Refer to the White Paper IHE ITI Access Control White Paper for further information about PEP and Access Control Systems).
Transactions
Authorization Decisions Query
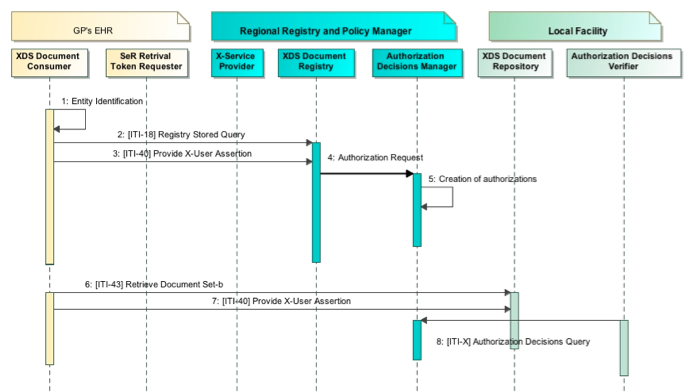
This transaction is used by the Authorization Decisions Verifier to query for authorization decisions, granted and managed by the Authorization Decisions Manager. These authorization decisions are created for an entity that is authorized to disclose specific documents. The Authorization Decisions Verifier asks for authorizations based on: the Requester Entity and the requested documents identifiers.
Relevant standards:
- OASIS SOAP v1.2
- OASIS Security Assertion Markup Language (SAML) v2.0
- OASIS eXtensible Access Control Markup Language (XACML) v2.0
- OASIS Multiple resource profile of XACML v2.0
- OASIS SAML 2.0 profile for XACML v2.0
- OASIS Cross-Enterprise Security and Privacy Authorization (XSPA) Profile of SAML v2.0 for Healthcare Version 2.0 (not normative)
Use-Case of Reference: Environment with a centralized Access Decision Manager Use Case Description
The XDS Document Repositories are all in the same XDS Affinity Domain, but are unable to perform access decisions. When an entity tries to retrieve some documents from an XDS Repository the XDS Document Repository lacks of the information needed to make an access control decision. The Authorization Decisions Manager can make the decision at the time of the query to the XDS Registry. This decision is enforced by the XDS Document Repository grouped with an Authorization Decisions Verifier. For example: Mr. White comes to his GP, Dr. Brown, to show him a Laboratory Report. This Laboratory Report is shared in a XDS infrastructure. Using his EHR, Dr. Brown queries for Mr. White’s Laboratory Reports shared in the XDS infrastructure. The Query Response returns some DocumentEntries to the XDS Document Consumer. Each XDSDocumentEntry in the response is authorized for the retrieval. Dr. Brown uses his XDS Document Consumer to retrieve these documents. XDS Document Repository verifies the authorization for the Requester Entity for each document requested before providing documents. No other access control decisions are needed at this level. Each Authorization Decision has a time slot of validity. Dr. Brown can retrieve documents until the Authorization expires. The Repository discloses only documents requested and authorized. There are conditions where XDS Document Repository might not be providing documents:
- The Requester Entity does not have authorization according to the Authorization Decisions Query
- The authorization was granted too long ago and the Authorization Decision is expired
The user attempting to retrieve from the XDS Document Repository is different from the user that was authorized (there is a mismatch between the user that performs the retrieve and the user that queries for documents).