ACWP Motivation
Revision as of 03:30, 15 January 2009 by Joerg.caumanns (talk | contribs) (→Needs-to-Know Principle)
IHE White Paper on Access Control
Motivation
Access Control vs. Perimeter Protection
Privacy and Data Security
Needs-to-Know Principle
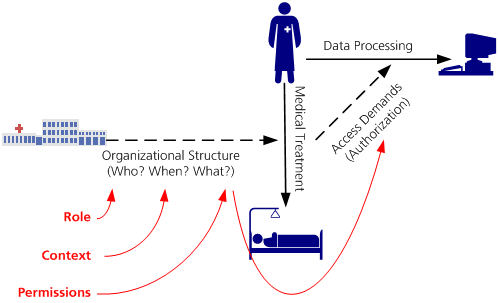
- the objective of access control is to enable every medical staff member to perform all data processing operations that he needs to do in order to fill his role within the medical treatment process - but no more!
- the organization of labour and separation of duty within a medical organization or a healthcare network determines who is allowed to perform what (medical) activities within which contexts (e. g. for what purpuses)
- Permissions for the processing of medical data are derived from the permitted activities of a role within a certain context. Following the needs-to-know principle these permissions reflect the operations on medical data which are part of the activity.
- Access control should always follow the needs-to-know principle. Therefore the objective is that the set of permitted operations of a user always contains the permissions that are required to fill the current job role.
- The needs-to-know principle couples permissions with the organization of labour. Therefore the permissions granted by an access control system that follows the needs-to-know principle are always as compliant with legal regulations and privacy restrictions as the underlying organization of work. If the orhganization of work within a medical organization or within amedical network violates legal regulations or a patient's consent, the access control system will implicitly do so as well.
- The needs-to-know principle has impact on the design of an access control system, because it differentiates between restrictions on the assignment of people to activities and restrictions on the accessability of medical data within certain activities. In an ideal access control system a patient consent should always focus on the first (e. g. by opting-in or -out certain people, job roles, or organizations from performing a medical activity) while resource protection should focus on the second (e. g. by stating clear rules which activities require which permissions).
Authors Note: We will come back to this during the discussion of the various access control paradigms, because this statement implies a strong relationship between patient consents and discretionary access control
Discussion
place issues to be discussed among the editorial team here...
Change Requests
place your change requests here...