Difference between revisions of "Audit Trail and Node Authentication"
JohnMoehrke (talk | contribs) |
JohnMoehrke (talk | contribs) |
||
| (46 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | __TOC__ | |
| − | + | ==Summary== | |
| + | |||
| + | The '''Audit Trail and Node Authentication (ATNA)''' Integration Profile establishes security measures which, together with the Security Policy and Procedures, provide patient information confidentiality, data integrity and user accountability. | ||
| + | |||
| + | ==Benefits== | ||
| + | |||
| + | '''Assistance to sites in implementing security and confidentiality policies''' | ||
| + | * This model is partially driven by the underlying assumption that there will be situations where documents are being exchanged between machines and stored on the recipient. This is partly driven by the need for healthcare systems to operate in disasters and overload situations, where the network operation is limited or destroyed. It is not safe to assume that clients are display only. So there will be semi-permanent copies of most information kept. Even in normal operation, healthcare providers may have only 15 minutes per patient. Good healthcare system design recognizes the need to not waste any of those seconds searching and transferring documents over a network. The documents are transferred in advance, and are kept locally until it is determined that they are no longer needed. There are thin client display only applications in healthcare, but they are limited to uses that can fail without introducing risks to safety or patient health, but a complete security/privacy design requires handling situations where data is stored after retrieval. | ||
| + | |||
| + | ==Details== | ||
| + | |||
| + | The '''Audit Trail and Node Authentication (ATNA) Integration Profile''': | ||
| + | contributes to access control by limiting network access between nodes and limiting access to each node to authorized users. Network communications between secure nodes in a secure domain are restricted to only other secure nodes in that domain. Secure nodes limit access to authorized users as specified by the local authentication and access control policy. | ||
| + | * User Authentication | ||
| + | The Audit Trail and Node Authentication Integration Profile requires only local user authentication. The profile allows each secure node to use the access control technology of its choice to authenticate users. The use of Enterprise User Authentication is one such choice, but it is not necessary to use this profile. | ||
| + | * Connection Authentication | ||
| + | The Audit Trail and Node Authentication Integration Profile requires the use of bi-directional certificate-based node authentication for connections to and from each node. The DICOM, HL7, and HTML protocols all have certificate-based authentication mechanisms defined. These authenticate the nodes, rather than the user. Connections to these machines that are not bi-directionally node-authenticated shall either be prohibited, or be designed and verified to prevent access to PHI. | ||
| + | * Audit Trails | ||
| + | User Accountability is provided through Audit Trail. The Audit Trail needs to allow a security officer in an institution to audit activities, to assess compliance with a secure domain’s policies, to detect instances of non-compliant behavior, and to facilitate detection of improper creation, access, modification and deletion of Protected Health Information (PHI). | ||
| − | == | + | ==Systems Affected== |
| − | + | Systems involved in this profile are: | |
| + | * Any local or enterprise-wide healthcare information systems that manage or process Protected Health Information | ||
| − | |||
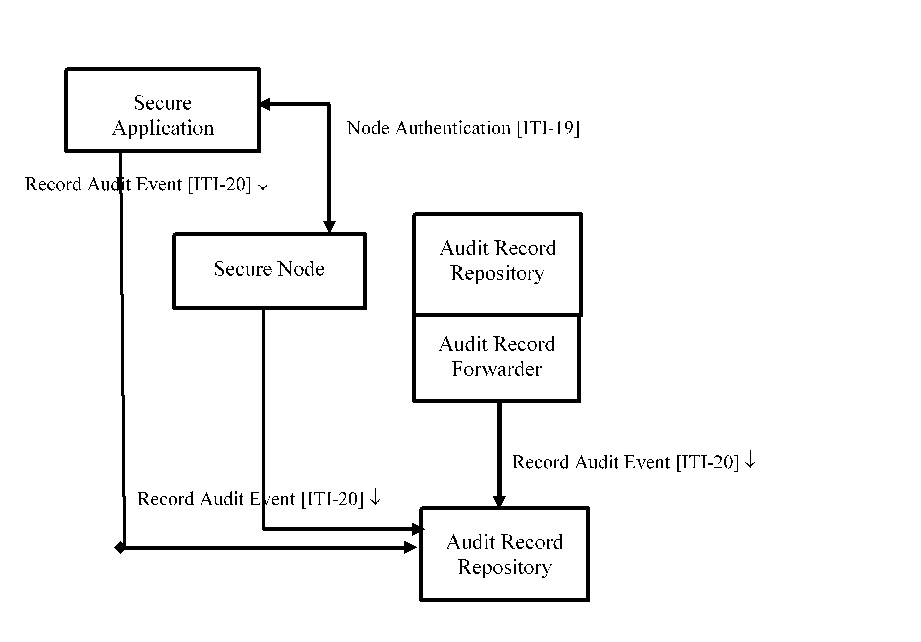
| − | + | '''Actors & Transactions:''' | |
| + | [[Image:ATNA-Actor-Transaction.jpg]] | ||
| − | == | + | ==Specification== |
| − | |||
| − | + | '''Profile Status:''' [[Comments| Final Text]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | '''Documents:''' | |
| − | + | [http://www.ihe.net/Technical_Framework/index.cfm#IT IHE IT Infrastructure Technical Framework Version 2 or later] | |
| − | + | :* [http://www.ihe.net/uploadedFiles/Documents/ITI/IHE_ITI_TF_Vol1.pdf#nameddest=30_Cross_Enterprise_Document_Won Vol. 1 - Section 9] | |
| − | + | :* [http://www.ihe.net/uploadedFiles/Documents/ITI/IHE_ITI_TF_Vol2a.pdf#nameddest=3_19_Authenticate_Node__ITI_19_ Vol. 2a - Sections 3.19], | |
| − | + | :* [http://www.ihe.net/uploadedFiles/Documents/ITI/IHE_ITI_TF_Vol2a.pdf#nameddest=3_20_Record_Audit_Event__ITI_20 Vol. 2a - Sections 3.20] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | '''Underlying Standards:''' | |
| − | '' | + | :* Secure Communications |
| + | :** [http://www.ietf.org/rfc/rfc2246.txt RFC 2246 Transport Layer Security (TLS) 1.0] | ||
| + | :** [http://www.ws-i.org/Profiles/BasicSecurityProfile-1.1.html WS-I Basic Security Profile 1.1] | ||
| + | :** [http://www.ietf.org/rfc/rfc3851.txt RFC 3851 Secure/Multipurpose Internet Mail Extensions (S/MIME) Version 3.1 Message Specification] | ||
| + | :** Encryption at least AES | ||
| + | :** Integrity at least SHA1 (HMAC or CBC) | ||
| + | :** Authentication at least RSA X.509 | ||
| + | :** Certificate encoded using at least BER and DER | ||
| + | :** Certificate validation required with support of both Direct Certificate and Chain of Trust to certificate Authority | ||
| + | :** Management of Trust is not further automated (see PWP and HPD profiles) | ||
| + | :* Audit Log Transport | ||
| + | :** RFC 5424 The Syslog Protocol | ||
| + | :** RFC 5425 Transmission of Syslog Messages over TLS | ||
| + | :** RFC 5426 Transmission of Syslog Messages over UDP | ||
| + | :** former -- IETF: The BSD Syslog Protocol. (RFC 3164) | ||
| + | :* Audit Log Message | ||
| + | :** Normative Specification for the Audit Log Message including Schema [http://medical.nema.org/medical/dicom/current/output/html/part15.html#sect_A.5 DICOM PS3.15 A.5] | ||
| + | :** Old Resources for historic reference | ||
| + | :*** Security Audit and Access Accountability Message XML Data Definitions for Healthcare Applications (RFC 3881). | ||
| + | :*** Currently being moved into ISO through TC 215 as (ISO/WD 27789) | ||
| + | :*** RFC 3881 schema http://www.xml.org/xml/schema/7f0d86bd/healthcare-security-audit.xsd --- REMOVED BY XML.ORG | ||
| + | :*** [http://medical.nema.org/standard.html DICOM - 2011 PS 3.15 (Part 15), Annex A.5 (ISO 12052)] ([ftp://medical.nema.org/medical/dicom/2011/ ftp]) -- Originally described by [[DICOM Supplement 95 | Supplement 95]] | ||
| + | :** DICOM OIDs for codeSystems used https://www.dabsoft.ch/dicom/6/A/ | ||
| − | == | + | ===Additional Supplements:=== |
| + | * [http://www.ihe.net/uploadedFiles/Documents/ITI/IHE_ITI_Suppl_RESTful-ATNA.pdf Add RESTful Query to ATNA] - Trial Implementation | ||
| − | + | '''Underlying Standards:''' | |
| + | * HL7 FHIR STU3 http://hl7.org/fhir/STU3 | ||
| + | ** AuditEvent | ||
| + | ** Bundle | ||
==See Also== | ==See Also== | ||
| − | |||
| − | + | This profile supports the security/privacy model discussed in [[IHE Security and Privacy for HIE]] white paper. | |
| + | |||
| + | See [[ATNA FAQ]] for implementation assistance, and [[ATNA Profile FAQ]] for other random help. | ||
| − | + | The 2008 connectathon tests for XDS related actors can be found at http://ihewiki.wustl.edu/wiki/index.php/XDS_Syslog_testing_requirements#Audit_log_requirements_for_XDS_at_2008_Connectathon | |
| − | + | [http://csrc.nist.gov/publications/nistpubs/800-92/SP800-92.pdf NIST SP800-92 Guide to Computer Security Log Management] | |
| − | + | NEMA White Paper on [http://www.medicalimaging.org/wp-content/uploads/2011/02/CertificateManagement-2007-05-Published.pdf Management of Machine Authentication Certificates] | |
| − | + | '''Related Profiles''' | |
| + | * [[Audit Trail and Node Authentication - Radiology Option]] extends ATNA with Radiology-specific audit trail messages. | ||
| + | * [[Consistent_Time | Consistent Time]] | ||
This page is based on the [[Profile Template]] | This page is based on the [[Profile Template]] | ||
| + | [[Category:Profiles]] | ||
| + | [[Category:ITI Profile]] | ||
| + | [[Category:FHIR]] | ||
| + | [[Category:Security]] | ||
| − | [[ | + | Current: [[Frameworks#IHE IT Infrastructure Technical Framework| IT Infrastructure Technical Framework]]. |
Revision as of 09:24, 29 August 2017
Summary
The Audit Trail and Node Authentication (ATNA) Integration Profile establishes security measures which, together with the Security Policy and Procedures, provide patient information confidentiality, data integrity and user accountability.
Benefits
Assistance to sites in implementing security and confidentiality policies
- This model is partially driven by the underlying assumption that there will be situations where documents are being exchanged between machines and stored on the recipient. This is partly driven by the need for healthcare systems to operate in disasters and overload situations, where the network operation is limited or destroyed. It is not safe to assume that clients are display only. So there will be semi-permanent copies of most information kept. Even in normal operation, healthcare providers may have only 15 minutes per patient. Good healthcare system design recognizes the need to not waste any of those seconds searching and transferring documents over a network. The documents are transferred in advance, and are kept locally until it is determined that they are no longer needed. There are thin client display only applications in healthcare, but they are limited to uses that can fail without introducing risks to safety or patient health, but a complete security/privacy design requires handling situations where data is stored after retrieval.
Details
The Audit Trail and Node Authentication (ATNA) Integration Profile: contributes to access control by limiting network access between nodes and limiting access to each node to authorized users. Network communications between secure nodes in a secure domain are restricted to only other secure nodes in that domain. Secure nodes limit access to authorized users as specified by the local authentication and access control policy.
- User Authentication
The Audit Trail and Node Authentication Integration Profile requires only local user authentication. The profile allows each secure node to use the access control technology of its choice to authenticate users. The use of Enterprise User Authentication is one such choice, but it is not necessary to use this profile.
- Connection Authentication
The Audit Trail and Node Authentication Integration Profile requires the use of bi-directional certificate-based node authentication for connections to and from each node. The DICOM, HL7, and HTML protocols all have certificate-based authentication mechanisms defined. These authenticate the nodes, rather than the user. Connections to these machines that are not bi-directionally node-authenticated shall either be prohibited, or be designed and verified to prevent access to PHI.
- Audit Trails
User Accountability is provided through Audit Trail. The Audit Trail needs to allow a security officer in an institution to audit activities, to assess compliance with a secure domain’s policies, to detect instances of non-compliant behavior, and to facilitate detection of improper creation, access, modification and deletion of Protected Health Information (PHI).
Systems Affected
Systems involved in this profile are:
- Any local or enterprise-wide healthcare information systems that manage or process Protected Health Information
Actors & Transactions:
Specification
Profile Status: Final Text
Documents: IHE IT Infrastructure Technical Framework Version 2 or later
Underlying Standards:
- Secure Communications
- RFC 2246 Transport Layer Security (TLS) 1.0
- WS-I Basic Security Profile 1.1
- RFC 3851 Secure/Multipurpose Internet Mail Extensions (S/MIME) Version 3.1 Message Specification
- Encryption at least AES
- Integrity at least SHA1 (HMAC or CBC)
- Authentication at least RSA X.509
- Certificate encoded using at least BER and DER
- Certificate validation required with support of both Direct Certificate and Chain of Trust to certificate Authority
- Management of Trust is not further automated (see PWP and HPD profiles)
- Audit Log Transport
- RFC 5424 The Syslog Protocol
- RFC 5425 Transmission of Syslog Messages over TLS
- RFC 5426 Transmission of Syslog Messages over UDP
- former -- IETF: The BSD Syslog Protocol. (RFC 3164)
- Audit Log Message
- Normative Specification for the Audit Log Message including Schema DICOM PS3.15 A.5
- Old Resources for historic reference
- Security Audit and Access Accountability Message XML Data Definitions for Healthcare Applications (RFC 3881).
- Currently being moved into ISO through TC 215 as (ISO/WD 27789)
- RFC 3881 schema http://www.xml.org/xml/schema/7f0d86bd/healthcare-security-audit.xsd --- REMOVED BY XML.ORG
- DICOM - 2011 PS 3.15 (Part 15), Annex A.5 (ISO 12052) (ftp) -- Originally described by Supplement 95
- DICOM OIDs for codeSystems used https://www.dabsoft.ch/dicom/6/A/
- Secure Communications
Additional Supplements:
- Add RESTful Query to ATNA - Trial Implementation
Underlying Standards:
- HL7 FHIR STU3 http://hl7.org/fhir/STU3
- AuditEvent
- Bundle
See Also
This profile supports the security/privacy model discussed in IHE Security and Privacy for HIE white paper.
See ATNA FAQ for implementation assistance, and ATNA Profile FAQ for other random help.
The 2008 connectathon tests for XDS related actors can be found at http://ihewiki.wustl.edu/wiki/index.php/XDS_Syslog_testing_requirements#Audit_log_requirements_for_XDS_at_2008_Connectathon
NIST SP800-92 Guide to Computer Security Log Management
NEMA White Paper on Management of Machine Authentication Certificates
Related Profiles
- Audit Trail and Node Authentication - Radiology Option extends ATNA with Radiology-specific audit trail messages.
- Consistent Time
This page is based on the Profile Template
Current: IT Infrastructure Technical Framework.